Lead2pass Dumps For Exam 400-251 With New Updated Exam Questions:
https://www.lead2pass.com/400-251.html
QUESTION 21
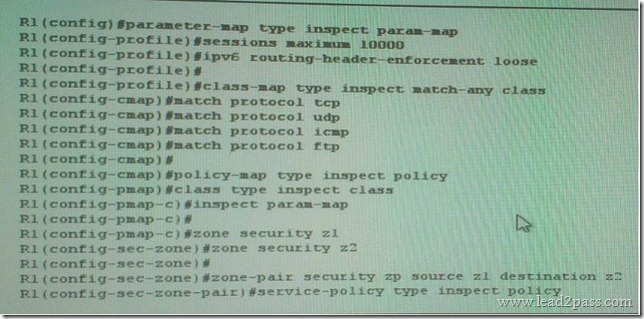
Refer to the exhibit which two statement about the given IPV6 ZBF configuration are true? (Choose two)
A. It provides backward compability with legacy IPv6 inspection
B. It inspect TCP, UDP,ICMP and FTP traffic from Z1 to Z2.
C. It inspect TCP, UDP,ICMP and FTP traffic from Z2 to Z1.
D. It inspect TCP,UDP,ICMP and FTP traffic in both direction between z1 and z2.
E. It passes TCP, UDP,ICMP and FTP traffic from z1 to z2.
F. It provide backward compatibility with legacy IPv4 inseption.
Answer: AB
QUESTION 22
In which class of applications security threads does HTTP header manipulation reside?
A. Session management
B. Parameter manipulation
C. Software tampering
D. Exception managements
Answer: B
Explanation:
http://www.cgisecurity.com/owasp/html/ch11s04.html
Session management doesn’t have anything to do with HTTP header
QUESTION 23
What is the most commonly used technology to establish an encrypted HTTP connection?
A. the HTTP/1.1 Upgrade header
B. the HTTP/1.0 Upgrade header
C. Secure Hypertext Transfer Protocol
D. HTTPS
Answer: D
QUESTION 24
What functionality is provided by DNSSEC?
A. origin authentication of DNS data
B. data confidentiality of DNS queries and answers
C. access restriction of DNS zone transfers
D. storage of the certificate records in a DNS zone file
Answer: A
QUESTION 25
What are the two mechanism that are used to authenticate OSPFv3 packets?(Choose two)
A. MD5
B. ESP
C. PLAIN TEXT
D. AH
E. SHA
Answer: BD
QUESTION 26
You have been asked to configure a Cisco ASA appliance in multiple mode with these settings:
(A) You need two customer contexts, named contextA and contextB
(B) Allocate interfaces G0/0 and G0/1 to contextA
(C) Allocate interfaces G0/0 and G0/2 to contextB
(D) The physical interface name for G0/1 within contextA should be “inside”.
(E) All other context interfaces must be viewable via their physical interface names.
If the admin context is already defined and all interfaces are enabled, which command set will complete this configuration?
A. context contextA
config-url disk0:/contextA.cfg
allocate-interface GigabitEthernet0/0 visible
allocate-interface GigabitEthernet0/1 inside
context contextB
config-url disk0:/contextB.cfg
allocate-interface GigabitEthernet0/0 visible
allocate-interface GigabitEthernet0/2 visible
B. context contexta
config-url disk0:/contextA.cfg
allocate-interface GigabitEthernet0/0 visible
allocate-interface GigabitEthernet0/1 inside
context contextb
config-url disk0:/contextB.cfg
allocate-interface GigabitEthernet0/0 visible
allocate-interface GigabitEthernet0/2 visible
C. context contextA
config-url disk0:/contextA.cfg
allocate-interface GigabitEthernet0/0 invisible
allocate-interface GigabitEthernet0/1 inside
context contextB
config-url disk0:/contextB.cfg
allocate-interface GigabitEthernet0/0 invisible
allocate-interface GigabitEthernet0/2 invisible
D. context contextA
config-url disk0:/contextA.cfg
allocate-interface GigabitEthernet0/0
allocate-interface GigabitEthernet0/1 inside
context contextB
config-url disk0:/contextB.cfg
allocate-interface GigabitEthernet0/0
allocate-interface GigabitEthernet0/2
E. context contextA
config-url disk0:/contextA.cfg
allocate-interface GigabitEthernet0/0 visible
allocate-interface GigabitEthernet0/1 inside
context contextB
config-url disk0:/contextB.cfg
allocate-interface GigabitEthernet0/1 visible
allocate-interface GigabitEthernet0/2 visible
Answer: A
QUESTION 27
Which statement about the cisco anyconnect web security module is true ?
A. It is VPN client software that works over the SSl protocol.
B. It is an endpoint component that is used with smart tunnel in a clientless SSL VPN.
C. It operates as an NAC agent when it is configured with the Anyconnect VPN client.
D. It is deployed on endpoints to route HTTP traffic to SCANsafe
Answer: D
QUESTION 28
Which two statements about the SeND protocol are true? (Choose two)
A. It uses IPsec as a baseline mechanism
B. It supports an autoconfiguration mechanism
C. It must be enabled before you can configure IPv6 addresses
D. It supports numerous custom neighbor discovery messages
E. It counters neighbor discovery threats
F. It logs IPv6-related threats to an external log server
Answer: BE
400-251 dumps full version (PDF&VCE): https://www.lead2pass.com/400-251.html
Large amount of free 400-251 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDU1JrNmttR1dfUm8