GreatExam 70-417 braindumps including the exam questions and the answer, completed by our senior IT lecturers and the Microsoft product experts, include the current newest 70-417 exam questions.
QUESTION 1
Your network contains an Active Directory domain named contoso.com.
The domain contains two domain controllers named DC1 and DC2.
You install Windows Server 2012 R2 on a new computer named DC3.
You need to manually configure DC3 as a domain controller.
Which tool should you use?
A. winrm.exe
B. Server Manager
C. dcpromo.exe
D. Active Directory Domains and Trusts
Answer: B
Explanation:
When you try to DCpromo a Server 2012, you get this message
QUESTION 2
Your network contains an Active Directory forest named contoso.com.
All domain controllers currently run Windows Server 2008 R2.
You plan to install a new domain controller named DC4 that runs Windows Server 2012 R2.
The new domain controller will have the following configurations:
– Schema master
– Global catalog server
– DNS Server server role
– Active Directory Certificate Services server role
You need to identify which configurations cannot be fulfilled by using the Active Directory Installation Wizard.
Which two configurations should you identify? (Each correct answer presents part of the solution.
Choose two.)
A. Enable the global catalog server.
B. Install the Active Directory Certificate Services role.
C. Transfer the schema master.
D. Install the DNS Server role.
Answer: BC
Explanation:
AD Installation Wizard will automatically install DNS and allows for the option to set it as a global catalog server. ADCS and schema must be done separately.
QUESTION 3
Your network contains an Active Directory forest.
The forest contains two domains named contoso.com and corp.contoso.com.
The forest contains four domain controllers.
The domain controllers are configured as shown in the following table.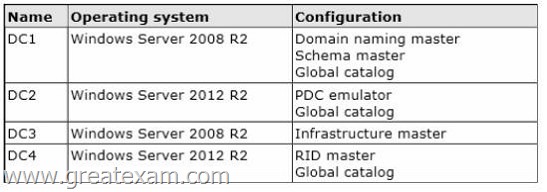
All domain controllers are DNS servers.
In the corp.contoso.com domain, you plan to deploy a new domain controller named DC5.
You need to identify which domain controller must be online to ensure that DC5 can be promoted successfully to a domain controller.
Which domain controller should you identify?
A. DC1
B. DC2
C. DC3
D. DC4
Answer: D
Explanation:
Relative ID (RID) Master:
Allocates active and standby RID pools to replica domain controllers in the same domain.
(corp.contoso.com) Must be online for newly promoted domain controllers to obtain a local RID pool that is required to advertise or when existing domain controllers have to update their current or standby RID pool allocation.
The RID master is responsible for processing RID pool requests from all domain controllers in a particular domain. When a DC creates a security principal object such as a user or group, it attaches a unique Security ID (SID) to the object.
This SID consists of a domain SID (the same for all SIDs created in a domain), and a relative ID (RID) that is unique for each security principal SID created in a domain. Each DC in a domain is allocated a pool of RIDs that it is allowed to assign to the security principals it creates.
When a DC’s allocated RID pool falls below a threshold, that DC issues a request for additional RIDs to the domain’s RID master. The domain RID master responds to the request by retrieving RIDs from the domain’s unallocated RID pool and assigns them to the pool of the requesting DC At any one time, there can be only one domain controller acting as the RID master in the domain.
The Infrastructure Master – The purpose of this role is to ensure that cross-domain objectreferences are correctly handled. For example, if you add a user from one domain to a security group from a different domain, the Infrastructure Master makes sure this is done properly.
As you can guess however, if your Active Directory deployment has only a single domain, then the Infrastructure Master role does no work at all, and even in a multi-domain environment it is rarely used except when complex user administration tasks are performed, so the machine holding this role doesn’t need to have much horsepower at all.
http://support.microsoft.com/kb/223346
http://en.wikipedia.org/wiki/Flexible_single_master_operation
QUESTION 4
Your network contain an active directory domain named Contoso.com.
The domain contains two servers named server1 and server2 that run Windows Server 2012 R2.
You create a security template named template1 by using the security template snap-in.
You need to apply template1 to server2.
Which tool should you use?
A. Security Templates
B. Computer Management
C. Security Configuration and Analysis
D. System Configuration
Answer: C
Explanation:
A. Template was already created – Provide standard security option to use in security policies
B. Needs to be applied at the GP level
C. Security templates are inactive until imported into a Group Policy object or the
SecurityConfiguration and Analysis
D. Tool to ID windows problems
http://technet.microsoft.com/en-us/library/jj730960.aspx
http://windows.microsoft.com/en-us/windows-vista/using-system-configuration
QUESTION 5
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4. Server1 is configured as shown in the following table.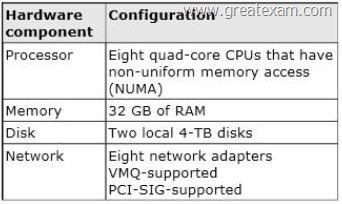
VM3 is used to test Applications.
You need to prevent VM3 from synchronizing its clock to Server1.
What should you configure?
A. NUMA topology
B. Resource control
C. Resource metering
D. Virtual Machine Chimney
E. The VLAN ID
F. Processor Compatibility
G. The startup order
H. Automatic Start Action
I. Integration Services
J. Port mirroring
K. Single-root I/O virtualization
Answer: I
Explanation:
Integration Services settings on virtual machines includes services such as operating system shutdown, time synchronization, data exchange, Heart beat, and Backup (volume snapshot services. Thus you should disable the time synchronization using Integration Services.
QUESTION 6
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4. Server1 is configured as shown in the following table.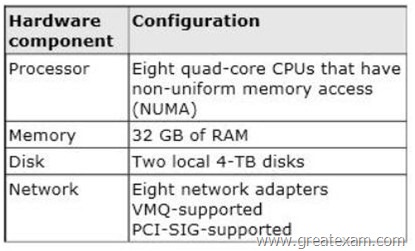
You plan to schedule a complete backup of Server1 by using Windows Server Backup.
You need to ensure that the state of VM1 is saved before the backup starts.
What should you configure?
A. NUMA topology
B. Resource control
C. Resource metering
D. Virtual Machine Chimney
E. The VLAN ID
F. Processor Compatibility
G. The startup order
H. Automatic Start Action
I. Integration Services
J. Port mirroring
K. Single-root I/O visualization
Answer: I
Explanation:
http://www.altaro.com/hyper-v/vss-crash-consistent-vs-Application-consistent-vss-backupspost-2-of-2/
Backup Operations in Hyper-V
No
VSS Writer Available?
In some cases, you need an Application-consistent backup but there is no VSS writer available. One example of this is MySQL. Hyper-V backups of virtual machines containing MySQL will always result in either a crashconsistent or an image-level backup. For MySQL, the latter is probably acceptable as MySQL doesn’t perpetually expand the log file. However, if you’re using MySQL within a VSS-aware VM, then a Hyper-Vbased backup tool is going to take a crash-consistent backup. MySQL (like any other database system) isn’t always recoverable from a crash-consistent backup; even when recovery is possible, it may be painful. MySQL is just one example; any number of line-of-business Applications could tell a similar tale. In the case of MySQL, one solution is to find a guest-level backup Application that is MySQL- aware and can back it up properly. For Applications for which no backup Application has a plug-in, you may need to have pre- and post-backup scripts that stop services or close Applications. If brief downtime is acceptable, you can disable the Backup item in Hyper-V Integration Services, thereby forcing Hyper-V to save the state of the VM during backup. This technique results in an image-level backup and can be used on any Application that doesn’t have a VSS writer.
QUESTION 7
Your network contains an Active Directory domain named contoso.com. The domain contains servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 has the IP Address Management (IPAM) Server feature installed.
You install the IPAM client on Server2.
You open Server Manager on Server2 as shown in the exhibit. (Click the Exhibit button.)
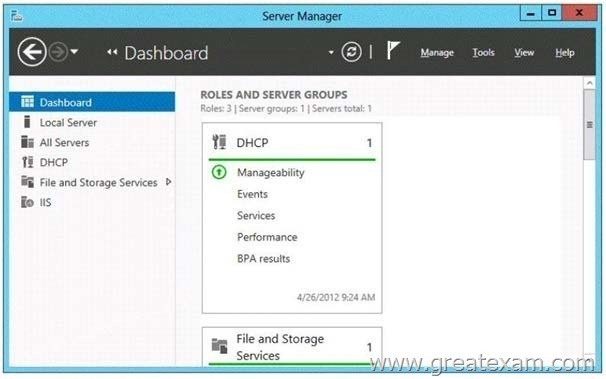
You need to manage IPAM from Server2. What should you do first?
A. On Server2, open Computer Management and connect to Server1.
B. On Server1, add the Server2 computer account to the IPAM ASM Administrators group.
C. On Server2, add Server1 to Server Manager.
D. On Server1, add the Server2 computer account to the IPAM MSM Administrators group.
Answer: C
Explanation:
In the exhibit, we can see that only one server is managed with Server Manager on Server2 (itself, as in a Server, Server Manager always contains at least the server itself):
So we can be sure that Server1 is not added to Server2 ServerManager Console. so if we want to manage IPAM, we should add Server1 to Server2’s Server Manager
http://technet.microsoft.com/en-us/library/hh831622.aspx
Step-by-Step: Configure IPAM to Manage
Your IP Address Space IP Address Management (IPAM) in Windows Server?2012 is a framework for discovering, monitoring, managing and auditing IP address space on a corporate network. IPAM provides the following features:
Automatic IP address infrastructure discovery
Highly customizable IP address space display, reporting, and management Configuration change auditing for DHCP and IPAM services Monitoring and management of DHCP and DNS services
IP address lease tracking
[…]
IPAM security groups
The following local IPAM security groups are created when you install IPAM. IPAM Users: Members of this group can view all information in server discovery, IP address space, and server management. They can view IPAM and DHCP server operational events, but cannot view IP address tracking information.
IPAM MSM Administrators: IPAM multi-server management (MSM) administrators have IPAM Users privileges and can perform IPAM common management tasks and server management tasks. IPAM ASM Administrators: IPAM address space management (ASM) administrators have IPAM Users privileges and can perform IPAM common management tasks and IP address space tasks. (that’s a user group, not a computer group) IPAM IP Audit Administrators:
Members of this group have IPAM Users privileges and can perform IPAM common management tasks and can view IP address tracking information.
IPAM Administrators: IPAM Administrators have the privileges to view all IPAM data and perform all IPAM tasks.
http://www.google.fr/url?sa=t&rct=j&q=&esrc=s&source=web&cd=2&cad=rja&ved=0CDwQFjAB&url=http%3A%2F%2Fdownload.microsoft.com%2Fdownload%2FF%2F6%2F9%2FF 69BE7E8-3E99-4A4A-
B1898AFADABC6216%2FUnderstand%2520and%2520Troubleshoot%2520IP%2520Address% 2520Management%2520(IPAM)%2520in%2520Windows%2520Server%25208%2520Beta .
docx&ei=5xXWUIzRAsaQhQeUz4GQCg&usg=AFQjCNGh5tHzxwcaU9vXDGmPUgtjfPvhn w&bvm=bv.1355534169,d.d2k
(download.microsoft.com)
Understand
and Troubleshoot IP Address Management (IPAM) in Windows Server 8 Beta If you are accessing the IPAM server remotely using ServerManager IPAM client RSAT, then you must be a member of the WinRMRemoteWMIUsers group on the IPAM server, in addition to being a member of the appropriate IPAM security group (or local Administrators group).
Installation Process ?IPAM Client
Although the IPAM client feature is automatically installed on a Windows Server “8” Beta server, along with installation of the IPAM Server feature, this component can also be installed or uninstalled on its own. Click through the Add roles and features wizard screens to select Role or Feature Based Install and the target server. On the Select Features screen, select Remote Server Administration Tools -> Feature Administration Tools -> IP Address Management (IPAM) Client. Click Add Features when prompted.
In order for the IPAM client to connect to an IPAM server, you must ensure that the target IPAM server is added to the Server Manager purview using the Add Servers wizard launched from the Manage menu. If both IPAM client and IPAM server are running on the same server, then by default the IPAM UI connects to the local IPAM server instance.
QUESTION 8
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named DC1 and a member server named Server1. Server1 has the IP Address Management (IPAM) Server feature installed.
On DC1, you configure Windows Firewall to allow all of the necessary inbound ports for IPAM.
On Server1, you open Server Manager as shown in the exhibit. (Click the Exhibit button.)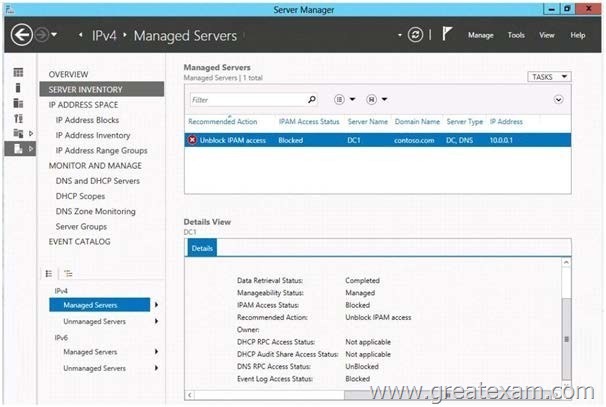
You need to ensure that you can use IPAM on Server1 to manage DNS on DC1.
What should you do?
A. Modify the outbound firewall rules on Server1.
B. Add Server1 to the Remote Management Users group.
C. Add Server1 to the Event Log Readers group.
D. Modify the inbound firewall rules on Server1.
Answer: C
Explanation:
The exhibit shows (in the details tab) that firewall rules are OK for DNS management (DNS RPC Access Status Unblocked) But it shows too that Event log Access Status is blocked (which by the way blocks the IPAM Access Status) => We should solve this by adding the Server1 computer account to the Event Log Readers group Understand and Troubleshoot IP Address Management (IPAM) in Windows Server 8 Beta (download.microsoft.com)
IPAM Access Monitoring
IPAM Access Settings
Manual provisioning
For manual provisioning, ensure that the required access settings are appropriately configured on the target server manually.
Verify Access Verify that IPAM access status is listed as unblocked indicating that manual or GPO based provisioning is successfully complete.
For the IPAM access status value to be allowed, all of the access sub-states shown in the details pane should be marked as allowed. These access states are:
DNS RPC access status
DHCP RPC access status
Event log access status
DHCP audit share access status
[…]
Troubleshooting Access Issues
If any of the access sub-states for managed server roles is showing in the Blocked state, check that the corresponding setting is enabled on the target server. For details of access setting to sub-state mapping refer to the IPAM Access Monitoring section in this guide. For GPO based provisioning, the GPResultcommand line tool can be used to troubleshoot group policy update issues. The provisioning task setup by IPAM DHCP and DNS GPOs creates a troubleshooting log in the location %windir%\temp named IpamDhcpLog.txt and IpamDnsLog.txt respectively.
http://social.technet.microsoft.com/Forums/en-US/winserver8gen/thread/c882c077-61bd45f6-ab47-735bd728d3bc/
IPAM
– Unblock access to a DC?
The
process to manually (not GPO based) unblock a DNS/DC server is:
1. Enable DNS RPC access by enabling the following inbound Firewall rules:
a) DNS Service (RPC)
b) DNS Service (RPC Endpoint Mapper)
2. Enable remote management access by enabling the following inbound Firewall rules:
a) Remote Service Management (RPC)
b) Remote Service Management (RPC-EPMAP)
3. Enable Remote Event Log Management RPC access by enabling the following inbound Firewall rules:
a) Remote Event Log Management (RPC)
b) Remote Event Log Management (RPC-EPMAP)
4. Add the IPAM machine acct to the Event Log Readers domain security group. See the example below.
This view is from Active Directory Users and Computers \ contoso.com \ Builtin \ Event Log Readers:
Also, there should be a Details tab at the bottom that summarizes whether or not the correct firewall ports and the Event Log Access status are unblocked.
QUESTION 9
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
The domain contains two servers named Server1 and Server2.
Both servers have the IP Address Management (IPAM) Server feature installed.
You have a support technician named Tech1.
Tech1 is a member of the IPAM Administrators group on Server1 and Server2.
You need to ensure that Tech1 can use Server Manager on Server1 to manage IPAM on Server2.
To which group on Server2 should you add Tech1? To answer, select the appropriate group in the answer area.
Answer:
QUESTION 10
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 has the IP Address Management (IPAM) Server feature installed.
IPAM is configured currently for Group Policy-based provisioning.
You need to change the IPAM provisioning method on Server1.
What should you do?
A. Run the ipamgc.exe command.
B. Run the Set-IPAMConfigurationcmdlet.
C. Reinstall the IP Address Management (IPAM) Server feature.
D. Delete IPAM Group Policy objects (GPOs) from the domain.
Answer: C
Explanation:
You cannot change the provisioning method after completing the initial setup.
When you install IPAM and configure either manual OR GPO, you receive the same message about not being able to change the provisioning method. As a matter of fact, I set it up in my lab and configured it as GPO. Here is a copy/paste of the message that is presently on the IPAM home page in server manager:
“The access configuration mode cannot be modified after completing the IPAM provisioning wizard” Also, the help console in IPAM displays this when searching about provisioning methods: “The managed server provisioning method cannot be changed after you complete the IPAM provisioning wizard.”
QUESTION 11
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Active Directory Federation Services (AD FS) server role installed.
Adatum.com is a partner organization.
You are helping the administrator of adatum.com set up a federated trust between adatum.com and contoso.com. The administrator of adatum.com asks you to provide a file containing the federation metadata ofcontoso.com.
You need to identify the location of the federation metadata file.
Which node in the AD FS console should you select? To answer, select the appropriate node in the answer area.
Answer: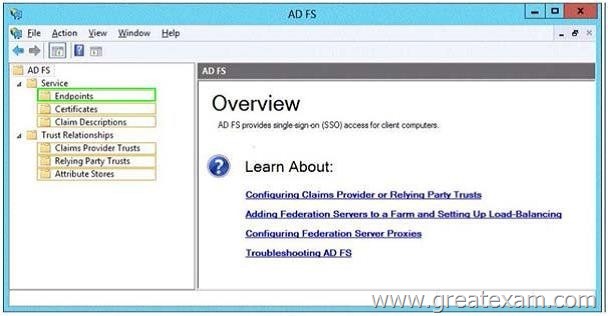
QUESTION 12
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
The domain contains an enterprise certification authority (CA).
The domain contains a server named Server1 that runs Windows Server 2012 R2.
You install the Active Directory Federation Services server role on Server1.
You plan to configure Server1 as an Active Directory Federation Services (AD FS) server.
The Federation Service name will be set to adfsl.contoso.com.
You need to identify which type of certificate template you must use to request a certificate for AD FS.
Which certificate template should you identify? To answer, select the appropriate template in the answer area.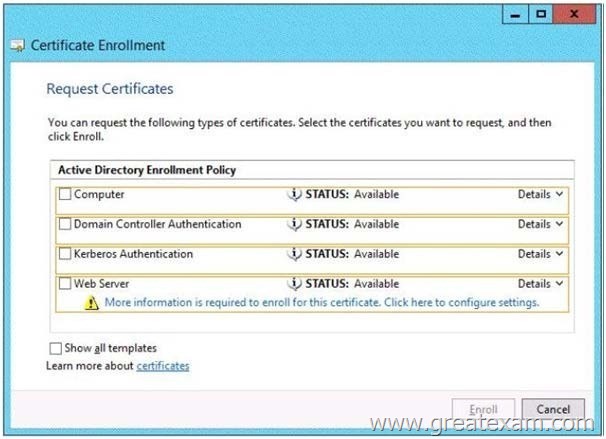
Answer: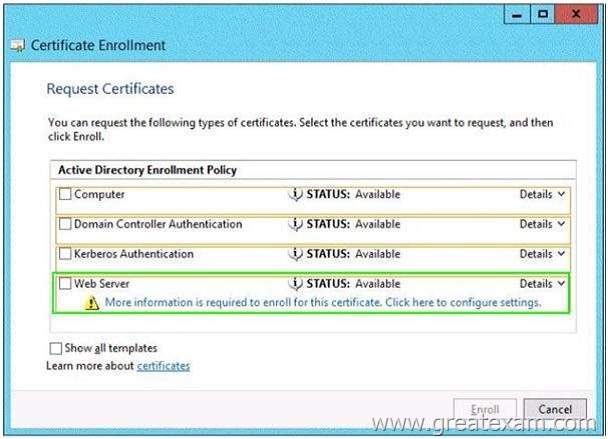
QUESTION 13
Your network contains an Active Directory domain named contoso.com.
The domain contains four servers.
The servers are configured as shown in the following table.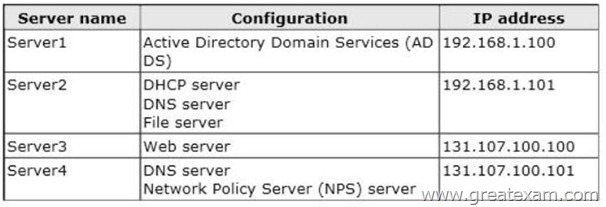
You plan to deploy an enterprise certification authority (CA) on a server named Servers.
Server5 will be used to issue certificates to domain-joined computers and workgroup computers.
You need to identify which server you must use as the certificate revocation list (CRL) distribution point for Server5.
Which server should you identify?
A. Server1
B. Server3
C. Server4
D. Server2
Answer: B
Explanation:
CDP (and AD CS) always uses a Web Server
NB: this CDP must be accessible from outside the AD, but here we don’t have to wonder about that as there’s only one web server.
http://technet.microsoft.com/fr-fr/library/cc782183%28v=ws.10%29.aspx
Selecting a CRL Distribution Point
Because CRLs are valid only for a limited time, PKI clients need to retrieve a new CRL periodically. Windows Server 2003 PKI Applications look in the CRL distribution point extension for a URL that points to a network location from which the CRL object can be retrieved. Because CRLs for enterprise CAs are stored in Active Directory, they can be accessed by means of LDAP. In comparison, because CRLs for stand-alone CAs are stored in a directory on the server, they can be accessed by means of HTTP, FTP, and so on as long as the CA is online. Therefore, you should set the CRL distribution point after the CA has been installed.
The system account writes the CRL to its distribution point, whether the CRL is published manually or is published according to an established schedule. Therefore you must ensure that the system accounts for CAs have permission to write to the CRL distribution point. Because the CRL path is also included in every certificate, you must define the CRL location and its access path before deploying certificates. If an Application performs revocation checking and a valid CRL is not available on the local computer, it rejects the certificate. You can modify the CRL distribution point by using the Certification Authority MMC snap-in. In this way, you can change the location where the CRL is published to meet the needs of users in your
organization.
You must move the CRL distribution point from the CA configuration folder to a Web server to change the location of the CRL, and you must move each new CRL to the new distribution point, or else the chain will break when the previous CRL expires.
Note
On root CAs, you must also modify the CRL distribution point in the CAPolicy.inf file so that the root CA certificate references the correct CDP and AIA paths, if specified. If you are using certificates on the Internet, you must have at least one HTTPs-accessible location for all certificates that are not limited to internal use.
http://technet.microsoft.com/en-us/library/cc771079.aspx
Configuring Certificate Revocation
It is not always possible to contact a CA or other trusted server for information about the validity of a certificate. To effectively support certificate status checking, a client must be able to access revocation data to determine whether the certificate is valid or has been revoked. To support a variety of scenarios, Active Directory Certificate Services (AD CS) supports industry-standard methods of certificate revocation. These include publication of certificate revocation lists (CRLs) and delta CRLs, which can be made available to clients from a variety of locations, including Active Directory Domain Services (AD DS), Web servers, and network file shares.
QUESTION 14
Your network contains three Active Directory forests.
Each forest contains an Active Directory Rights Management Services (AD RMS) root cluster.
All of the users in all of the forests must be able to access protected content from any of the forests.
You need to identify the minimum number of AD RMS trusts required.
How many trusts should you identify?
A. 2
B. 3
C. 4
D. 6
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/dd772648%28v=ws.10%29.aspx
AD RMS Multi-forest Considerations
QUESTION 15
Your network contains an Active Directory domain named contoso.com.
The network contains a file server named Server1 that runs Windows Server 2012 R2.
You create a folder named Folder1.
You share Folder1 as Share1. The NTFS permissions on Folder1 are shown in the Folder1 exhibit. (Click the Exhibit button.)
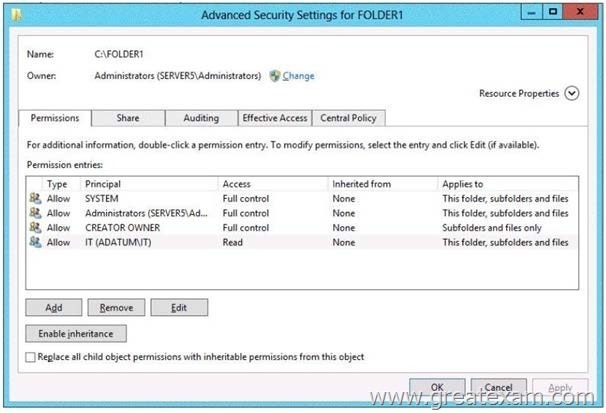
The Everyone group has the Full control Share permission to Folder1.
You configure a central access policy as shown in the Central Access Policy exhibit. (Click the Exhibit button.)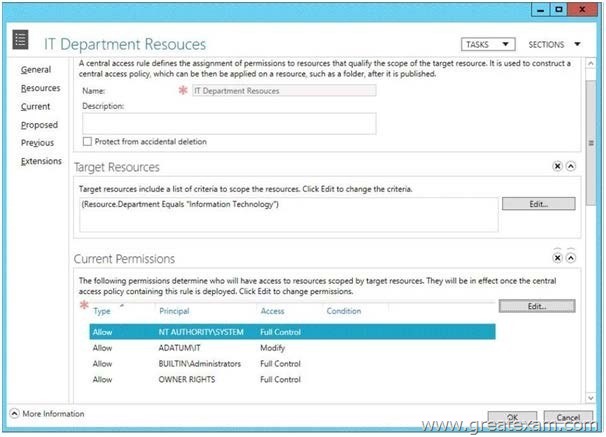
Members of the IT group report that they cannot modify the files in Folder1.
You need to ensure that the IT group members can modify the files in Folder1.
The solution must use central access
policies to control the permissions.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. On the Security tab of Folder1, remove the permission entry for the IT group.
B. On the Classification tab of Folder1, set the classification to “Information Technology”.
C. On the Security tab of Folder1, assign the Modify permission to the Authenticated Users group.
D. On Share1, assign the Change Share permission to the IT group.
E. On the Security tab of Folder1, add a conditional expression to the existing permission entry for
the IT group.
Answer: BC
Explanation:
NB added the missing exhibits by searching for a piece of the question on google
=> i did get an answer (a pdf file with a few questions and exhibits, but how to be sure they’re ok…)
initial Answer:
On the Classification tab of Folder1, set the classification to Information Technology. =>true On the Security tab of Folder1, add a conditional expression to the existing permission entry for the IT group. =>false it took me a whole day and a hole night to find that, but now i’m sure of the answer. Let me explain my point of view You first set the Folder1 classification to “Information Technology” so it meets the target resource requirement and the Central Access Policy can be Applied to it, no problem about that.
But my problem is about the second answer, to me none of them is good :
A: On the Security tab of Folder1, remove the permission entry for the IT group. => tested => it failed of course, users don’t even have read permissions anymore
D: On Share1, assign the Change share permission to the IT group =>Everyone already has the full control share permission => won’t solve the problem which is about the NTFS Read permission
E: On the Security tab of Folder1, add a conditional expression to the existing permission entry for the IT group => how could a condition, added to a read permission, possibly transform a read to a modify permission? if they had said “modify the permission and add a conditional expression” => ok (even if that’s stupid, it works) a condition is Applied to the existing permissions to filter existing access to only matching users or groups so if we Apply a condition to a read permission, the result will only be that less users (only them matching the conditions) will get those read permissions, which actually don’t solve the problem neither so only one left :
C: On the Security tab of Folder1, assign the Modify permission to the Authenticated Users group => for sure it works and it’s actually the only one which works, but what about security? well i first did not consider this method => “modify” permission for every single authenticated users? But now it looks very clear :
THE MORE RESTRICTIVE PERMISSION IS ALWAYS THE ONE APPLIED!! So “Modify” for Authenticated Users group and this will be filtered by the DAC who only allows IT group. and it matches the current settings that no other user (except admin, creator owner, etc…) can even read the folder. and this link confirms my theory :
http://autodiscover.wordpress.com/2012/09/12/configuring-dynamic-access-controls-andfile-classificationpart4-winservr-2012-dac-microsoft-mvpbuzz/
Configuring Dynamic Access Controls and File Classification
Note:
In order to allow DAC permissions to go into play, allow everyone NTFS full control permissions and then DAC will overwrite it, if the user doesn’t have NTFS permissions he will be denied access even if DAC grants him access.
And
if this can help, a little summary of configuring DAC:
QUESTION 16
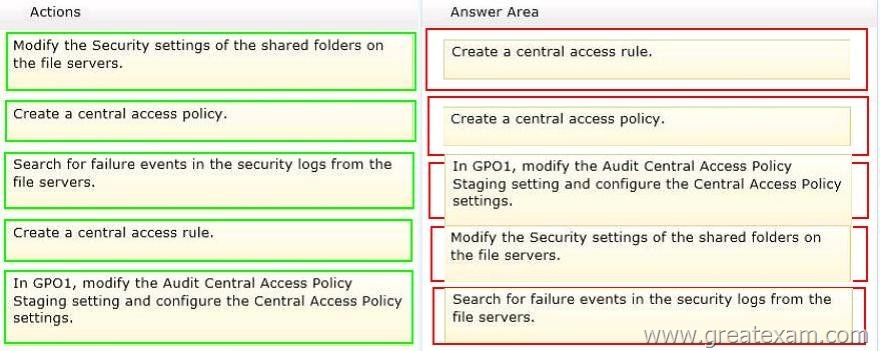
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
All file servers in the domain run Windows Server 2012 R2.
The computer accounts of the file servers are in an organizational unit (OU) named OU1.
A Group Policy object (GPO) named GP01 is linked to OU1.
You plan to modify the NTFS permissions for many folders on the file servers by using central access policies.
You need to identify any users who will be denied access to resources that they can currently access once the new permissions are implemented.
In which order should you perform the five actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
QUESTION 17
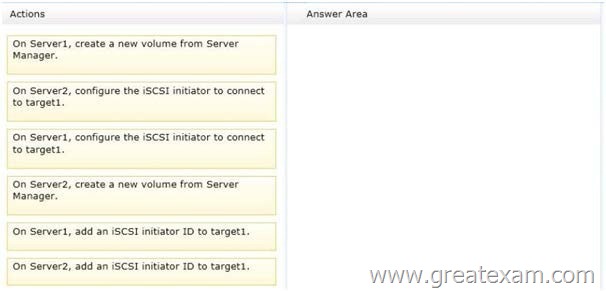
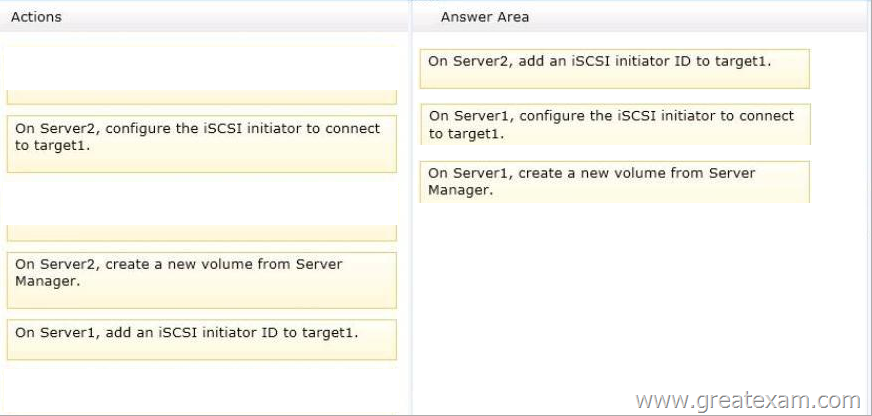
Drag and Drop Question
You have a server named Server2 that runs Windows Server 2012 R2.
You need to configure the storage so that it appears in Windows Explorer as a drive letter on Server1.
Which three actions should you perform in sequence? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
QUESTION 18
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
The domain contains a file server named Server1.
All servers run Windows Server 2012 R2.
All domain user accounts have the Division attribute automatically populated as part of the user provisioning process.
The Support for Dynamic Access Control and Kerberos armoring policy is enabled for the domain.
You need to control access to the file shares on Server1 based on the values in the Division attribute and the Division resource property.
Which three actions should you perform in sequence? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Answer: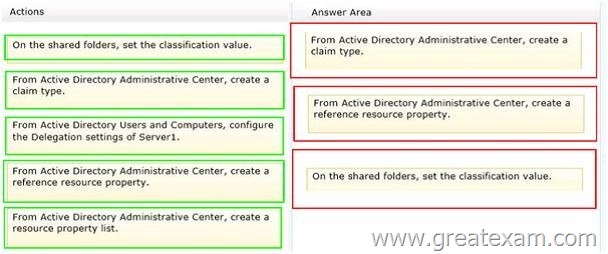
QUESTION 19
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Both servers have the Hyper-V server role installed.
Server1 and Server2 are located in different offices.
The offices connect to each other by using a high-latency WAN link.
Server2 hosts a virtual machine named VM1.
You need to ensure that you can start VM1 on Server1 if Server2 fails.
The solution must minimize hardware costs.
What should you do?
A. On Server2, install the Multipath I/O (MPIO) feature.
Modify the storage location of the VHDs for VM1.
B. From the Hyper-V Settings of Server1, modify the Replication Configuration settings.
Enable replication for VM1.
C. On Server1, install the Multipath I/O (MPIO) feature.
Modify the storage location of the VHDs for VM1.
D. From the Hyper-V Settings of Server2, modify the Replication Configuration settings.
Enable replication for VM1.
Answer: B
Explanation:
You first have to enable replication on the Replica server–Server1–by going to the server and modifying the”Replication Configuration” settings under Hyper-V settings.
You then.go to VM1– which presides on Server2–and run the “Enable Replication” wizard on VM1.
QUESTION 20
You have a server named File1 that runs Windows Server 2012 R2. File1 has the File Server role service installed.
You plan to back up all shared folders by using Microsoft Online Backup.
You download and install the Microsoft Online Backup Service Agent on File1.
You need to ensure that you use Windows Server Backup to back up data to Microsoft Online Backup.
What should you do?
A. From Computer Management, add the File1 computer account to the Backup Operators group.
B. From the Services console, modify the Log On settings of the Microsoft Online Backup Service Agent.
C. From Windows Server Backup, run the Register Server Wizard.
D. From a command prompt, run wbadmin.exe enable backup.
Answer: C
Explanation:
Download and install the Windows Azure Online Backup Agent After you create an account on the Windows Azure Online Backup website, you can download the Windows Azure Online Backup Agent and install it locally.
An Online Backup node then appears in the navigation pane of the Windows Server Backup console, as shown in Figure 12-
If you prefer, you can also configure online backups from the Windows Azure Online Backup console, which becomes available after you install the agent. The Windows Azure Online Backup console provides exactly the same set of options as the Online Backup node in the Windows Server Backup console.
Register server The next step is to register your server. Registering a server enables you to perform backups from that same server only. (Remember this point for the exam.) To register the server, from the Actions menu, select Register Server.
The Register Server Wizard includes two configuration steps. First, you are given an opportunity to specify a proxy server if desired. Second, you are asked to provide a passphrase that will be used to encrypt your backup data and a location to save this passphrase in a file.
You need to provide this passphrase when you perform a restore operation, so it’s essential that you don’t lose it. (Microsoft doesn’t maintain a copy of your passphrase.) A Generate Passphrase option creates the passphrase for you automatically. After you register a server, new options for Online Backup appear in the Actions pane, including Schedule Backup, Recover Data, Change Properties, and Unregister Server.
If you use GreatExam braindump as your 70-417 exam prepare material, we guarantee your success in the first attempt. GreatExam 70-417 practice test provides you everything you will need to take your 70-417 Exam.