Are you worring about the 70-413 exam? GreatExam provides the latest 70-413 braindumps and guarantees you passing 70-413 exam beyond any doubt.
QUESTION 101
Your company plans to deploy a remote access solution to meet the following requirements:
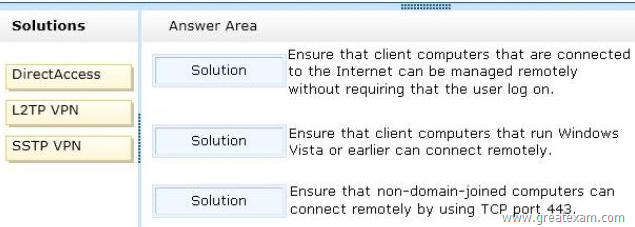
– Ensure that client computers that are connected to the Internet can be managed remotely without requiring that the user log on.
– Ensure that client computers that run Windows Vista or earlier can connect remotely.
– Ensure that non-domain-joined computers can connect remotely by using TCP port 443.
You need to identify which remote access solutions meet the requirements.
Which solutions should you identify? To answer, drag the appropriate solution to the correct requirement in the answer area. Each solution may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Answer: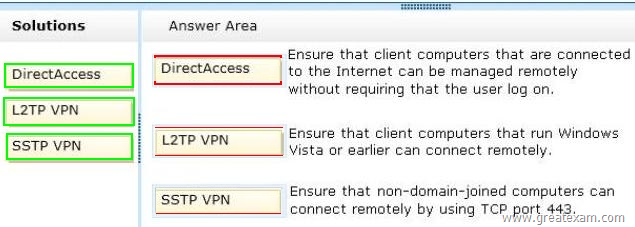
Explanation:
– DirectAccess, introduced in the Windows 7 and Windows Server 2008 R2 operating systems, allows remote users to securely access enterprise shares, web sites, and applications without connecting to a virtual private network (VPN). DirectAccess establishes bi-directional connectivity with a user’s enterprise network every time a user’s DirectAccess-enabled portable computer connects to the Internet, even before the user logs on. Users never have to think about connecting to the enterprise network and IT administrators can manage remote computers outside the office, even when the computers are not connected to the VPN. Forefront Unified Access Gateway (UAG) 2010 extends the benefits of DirectAccess across your infrastructure, enhancing scalability and simplifying deployment and ongoing management.
– Both L2TP and IPsec must be supported by both the VPN client and the VPN server. Client support for L2TP is built in to the Windows Vista® and Windows XP remote access clients, and VPN server support for L2TP is built in to members of the Windows Server® 2008 and Windows Server 2003 family.
– Secure Socket Tunneling Protocol (SSTP) is a form of VPN tunnel that provides a mechanism to transport PPP or L2TP traffic through an SSL 3.0 channel. SSL provides transport-level security with key-negotiation, encryption and traffic integrity checking. The use of SSL over TCP port 443 allows SSTP to pass through virtually all firewalls and proxy servers.
QUESTION 102
Your network contains an Active Directory domain named contoso.com.
The domain contains three Active Directory sites.
The Active Directory sites are configured as shown in the following table.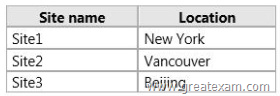
The sites connect to each other by using the site links shown in the following table.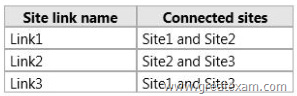
You need to design the Active Directory site topology to meet the following requirements:
– Ensure that all replication traffic between Site2 and Site3 replicates through Site1 if a domain controller in Site1 is available.
– Ensure that the domain controllers between Site2 and Site3 can replicate if all of the domain controllers in Site1 are unavailable.
What should you do?
A. Delete Link2.
B. Disable site link bridging.
C. Delete Link3.
D. Create one site link bridge.
Answer: D
QUESTION 103
Your network contains a server named Server1 that runs Windows Server 2012.
Server1 is configured as a Hyper-V host. Server1 hosts a virtual machine named VM1.
VM1 is configured as a file server that runs Windows Server 2012.
VM1 connects to a shared storage device by using the iSCSI Initiator.
You need to back up the files and the folders in the shared storage used by VM1.
The solution must ensure that open files are included in the backup.
What should you do?
A. From Hyper-V Manager, create a snapshot of VM1.
B. From Server1, perform a backup by using Windows Server Backup.
C. From VM1, perform a backup by using Windows Server Backup.
D. From Microsoft System Center 2012 Virtual Machine Manager (VMM), create a copy of VM1.
Answer: C
Explanation:
Backing Up Hyper-V Virtual Machines Using Windows Server Backup
http://blogs.msdn.com/b/taylorb/archive/2008/08/20/backing-up-hyper-v-virtual-machines-using-windowsserver-backup.aspx
QUESTION 104
Your company has a main office and a branch office.
The network contains an Active Directory domain named contoso.com.
The domain contains three domain controllers.
The domain controllers are configured as shown in the following table.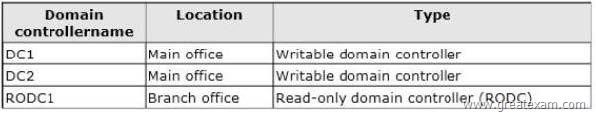
The domain contains two global groups.
The groups are configured as shown in the following table.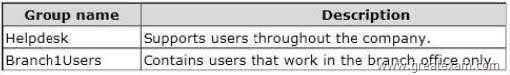
You need to ensure that the RODC is configured to meet the following requirements:
– Cache passwords for all of the members of Branch1Users.
– Prevent the caching of passwords for the members of Helpdesk.
What should you do?
A. Create a Password Settings object (PSO) for the Helpdesk group.
B. Install the BranchCache feature on RODC1.
C. Modify the password replication policy of RODC1.
D. Modify the delegation settings of RODC1.
Answer: C
QUESTION 105
Your company has a main office, ten regional datacenters; and 100 branch offices.
You are designing the site topology for an Active Directory forest named contoso.com.
The forest will contain the following servers:
– In each regional datacenter and in the main office, a domain controller that runs Windows Server
– In each branch office, a file server that runs Windows Server 2012
You have a shared folder that is accessed by using the path \\contoso.com\shares\software.
The folder will be replicated to a local file server in each branch office by using Distributed File System (DFS) replication.
You need to recommend an Active Directory site design to meet the following requirements:
– Ensure that users in the branch offices will be authenticated by a domain controller in the closest regional datacenter.
– Ensure that users automatically connect to the closest file server when they access \\contoso.com\shares\software.
How many Active Directory sites should you recommend?
A. 1
B. 10
C. 11
D. 111
Answer: C
Explanation:
As each branch office will have its own subnet and each site will have a subnet range associated with it. The regional datacentre subnet will also fall within the scope of the site subnet range. Therefore branch office PCs will become site aware and linked with their regional datacentre via site/subnet association.
As Authentication will occur at the DC in the same site (As long as the DC is online of course) The users will authenticate at their closest regional datacentre
As DFS is site aware and has the ability to set referral ordering you can force each client to refer to its local DFS file server in its own site and as there are no file servers in the regional datacentres this means the local branch file server will be chosen.
QUESTION 106
Your network contains an Active Directory forest named contoso.com.
Your company merges with another company that has an Active Directory forest named litwareinc.com.
Each forest has one domain.
You establish a two-way forest trust between the forests.
The network contains three servers.
The servers are configured as shown in the following table.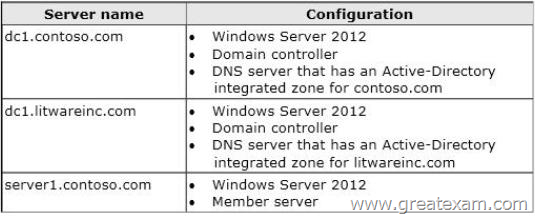
You confirm that the client computers in each forest can resolve the names of the client computers in both forests.
On dc1.litwareinc.com, you create a zone named GlobalNames.
You need to recommend changes in both forests to ensure that the users in both forests can resolve single-label names by using the GlobalNames zone in litwareinc.com.
Which changes should you recommend? To answer, drag the appropriate configuration to the correct server in the answer area. Each configuration may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.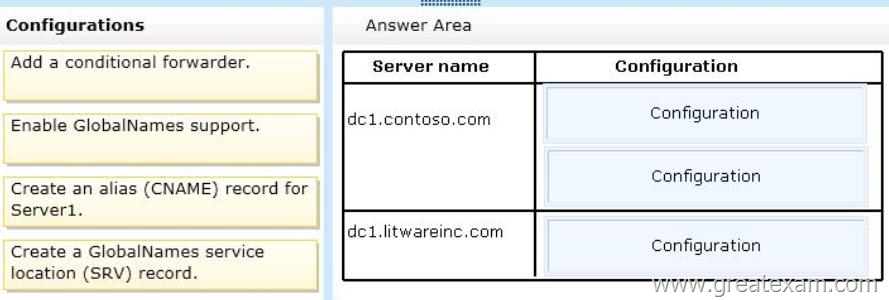
Answer: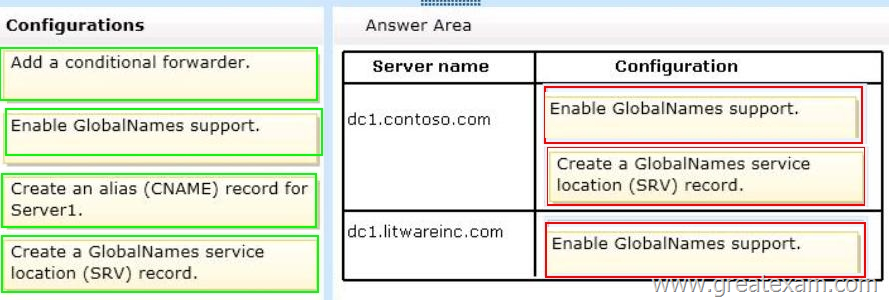
QUESTION 107
Your network contains an Active Directory domain named contoso.com.
Your company has an enterprise root certification authority (CA) named CA1.
You plan to deploy Active Directory Federation Services (AD FS) to a server named Serverl.
The company purchases a Microsoft Office 365 subscription.
You plan register the company’s SMTP domain for Office 365 and to configure single sign-on for all users.
You need to identify which certificate or certificates are required for the planned deployment. Which certificate or certificates should you identify? (Each correct answer presents a complete solution. Choose all that apply.)
A. a server authentication certificate that is issued by a trusted third-party root CA and that contains the subject name serverl.contoso.com
B. a server authentication certificate that is issued by CA1 and that contains the subject name Server1
C. a server authentication certificate that is issued by a trusted third-party root CA and that contains the subject name Server1
D. a server authentication certificate that is issued by CA1 and that contains the subject name serverl.contoso.com
E. self-signed server authentication certificates for serverl.contoso.com
Answer: DE
Explanation:
Use the full name.
The subject name is commonly represented by using an X.500 or Lightweight Directory Access Protocol (LDAP) format.
QUESTION 108
Your company has a main office and a branch office.
The network contains an Active Directory domain named contoso.com.
The domain contains three domain controllers.
The domain controllers are configured as shown in the following table.
The domain contains two global groups.
The groups are configured as shown in the following table.
You need to ensure that the RODC is configured to meet the following requirements:
– Cache passwords for all of the members of Branch1Users.
– Prevent the caching of passwords for the members of Helpdesk.
What should you do?
A. Create a Password Settings object (PSO) for the Helpdesk group.
B. Install the BranchCache feature on RODC1.
C. Modify the delegation settings of RODC1.
D. Modify the membership of the Denied RODC Password Replication group.
Answer: D
Explanation:
Password Replication Policy Allowed and Denied lists Two new built-in groups are introduced in Windows Server 2008 Active Directory domains to support RODC operations. These are the Allowed RODC Password Replication Group and Denied RODC Password Replication Group.
These groups help implement a default Allowed List and Denied List for the RODC Password Replication Policy. By default, the two groups are respectively added to the msDS- RevealOnDemandGroup and msDS-NeverRevealGroup Active Directory attributes.
QUESTION 109
Your company has a main office and 20 branch offices.
All of the offices connect to each other by using a WAN link.
The network contains an Active Directory forest named contoso.com.
The forest contains a domain for each office.
The forest root domain contains all of the server resources.
Each branch office contains two domain controllers for the branch office domain and one domain controller for the contoso.com domain.
Each branch office has a support technician who is responsible for managing the accounts of their respective office only.
You recently updated all of the WAN links to high-speed WAN links.
You need to recommend changes to the Active Directory infrastructure to meet the following requirements:
– Reduce the administrative overhead of moving user accounts between the offices.
– Ensure that the support technician in each office can manage the user accounts of their respective office.
What should you include in the recommendation? More than one answer choice may achieve the goal. Select the BEST answer.
A. Create shortcut trusts between each child domain.
In the main office, add a domain controller to each branch office domain.
B. Create a new child domain named corp.contoso.com.
Create a shortcut trust between each child domain and corp.contoso.com.
C. Move all of the user accounts of all the branch offices to the forest root domain.
Decommission all of the child domains.
D. Create a new forest root domain named contoso.local.
Move all of the user accounts of all the branch offices to the new forest root domain.
Decommission all of the child domains.
Answer: C
Explanation:
The most basic of all Active Directory structures is the single domain model; this type of domain structure comes with one major advantage over the other models:
simplicity. A single security boundary defines the borders of the domain, and all objects are located within that boundary. The establishment of trust relationships between other domains is not necessary, and implementation of technologies such as Group Policies is made easier by the simple structure.
QUESTION 110
Your company, which is named Contoso, Ltd., has a main office and two branch offices.
The main office is located in North America.
The branch offices are located in Asia and Europe.
You plan to design an Active Directory forest and domain infrastructure.
You need to recommend an Active Directory design to meet the following requirements:
– The contact information of all the users in the Europe office must not be visible to the users in the other offices.
– The administrators in each office must be able to control the user settings and the computer settings of the users in their respective office.
– The solution must use the least amount of administrative effort.
What should you include in the recommendation?
A. One forest that contains three domains
B. One forest that contains one domain
C. Three forests that each contain one domain
D. Two forests that each contain one domain
Answer: B
Explanation:
The solution must use the least amount of administrative effort.
http://www.informit.com/articles/article.aspx?p=32080&seqNum=5
QUESTION 111
Your network contains an Active Directory forest named contoso.com.
You plan to deploy 200 Hyper-V hosts by using Microsoft System Center 2012 Virtual Machine Manager (VMM) Service Pack 1 (SP1).
You add a PXE server to the fabric.
You need to identify which objects must be added to the VMM library for the planned deployment. What should you identify? (Each correct answer presents part of the solution. Choose all that apply.)
A. A host profile
B. A capability profile
C. A hardware profile
D. A generalized image
E. A service template
Answer: AD
Explanation:
Templates and profiles are used to standardize the creation of virtual machines and services.
These configurations are stored in the VMM database but are not represented by physical configuration files.
There are several new types of templates and profiles in VMM, most of which are used for service creation.
There are also host profiles, used for deploying a Hyper-V host from a bare-metal computer, and capability profiles, used to specify the capabilities of virtual machines on each type of supported hypervisor when virtual machines are deployed to a private cloud.
Note:
– host profile:
A Virtual Machine Manager library resource that contains hardware and operating system configuration settings to convert a bare-metal computer to a managed Hyper-V host.
– capability profile:
A Virtual Machine Manager library resource that defines which resources (for example, number of processors or maximum memory) are available to a virtual machine that is created in a private cloud.
– Incorrect: service template:
A Virtual Machine Manager library resource that contains the configuration settings used to deploy each tier of a service.
Reference:Technical Documentation for System Center2012 Virtual Machine Manager
QUESTION 112
You plan to deploy multiple servers in a test environment by using Windows Deployment Services (WDS).
You need to identify which network services must be available in the test environment to deploy the servers.
Which network services should you identify? (Each correct answer presents part of the solution.Choose ail that apply.)
A. DHCP
B. Active Directory Domain Services (AD DS)
C. DNS
D. Active Directory Lightweight Directory Services (AD LDS)
E. WINS
F. Network Policy Server (NPS)
Answer: AC
Explanation:
http://technet.microsoft.com/en-us/library/hh831764.aspx
QUESTION 113
Your network contains an Active Directory forest named contoso.com.
The forest is managed by using Microsoft System Center 2012.
Web developers must be able to use a self-service portal to request the deployment of virtual machines based on predefined templates.
The requests must be approved by an administrator before the virtual machines are deployed.
You need to recommend a solution to deploy the virtual machines.
What should you include in the recommendation? More than one answer choice may achieve the goal. Select the BEST answer.
A. A Virtual Machine Manager (VMM) service template, a Service Manager service offering, and an Orchestrator runbook
B. A Virtual Machine Manager (VMM) service template, an Operations Manager dashboard, and an Orchestrator runbook
C. A Service Manager service offering, an Orchestrator runbook, and Configuration Manager packages
D. A Service Manager service offering, an Orchestrator runbook, and an Operations Manager dashboard
Answer: A
QUESTION 114
You have a server named Server1 that runs Windows Server 2012.
Server1 has the DNS Server server role installed.
You need to recommend changes to the DNS infrastructure to protect the cache from cache poisoning attacks.
What should you configure on Server1?
A. DNS devolution
B. DNS Security Extensions (DNSSEC)
C. DNS cache locking
D. The global query block list
Answer: C
QUESTION 115
Your network contains an Active Directory domain named contoso.com.
All client computers run either Windows 7 or Windows 8.
Some users work from customer locations, hotels, and remote sites.
The remote sites often have firewalls that limit connectivity to the Internet.
You need to recommend a VPN solution for the users.
Which protocol should you include in the recommendation?
A. L2TP/IPSec
B. PPTP
C. IKEV2
D. SSTP
Answer: D
Explanation:
Secure Socket Tunneling Protocol (SSTP) is a form of VPN tunnel that provides a mechanism to transport PPP or L2TP traffic through an SSL 3.0 channel. SSL provides transport-level security with key-negotiation, encryption and traffic integrity checking. The use of SSL over TCP port 443 allows SSTP to pass through virtually all firewalls and proxy servers except for authenticated web proxies.
https://en.wikipedia.org/wiki/Secure_Socket_Tunneling_Protocol
QUESTION 116
Your network contains an Active Directory domain named contoso.com.
Your company has 100 users in the sales department.
Each sales user has a domain-joined laptop computer that runs either Windows 7 or Windows 8. The sales users rarely travel to the company’s offices to connect directly to the corporate network.
You need to recommend a solution to ensure that you can manage the sales users’ laptop computers when the users are working remotely.
What solution should you include in the recommendation?
A. Deploy a Microsoft System Center 2012 Service Manager infrastructure.
B. Deploy the Remote Access server role on a server on the internal network.
C. Deploy the Network Policy and Access Services server role on a server on the internal network.
D. Deploy a Microsoft System Center 2012 Operations Manager infrastructure.
Answer: B
Explanation:
In Windows Server® 2012 R2 and Windows Server® 2012 the Remote Access server role provides centralized administration, configuration, and monitoring of both DirectAccess and VPN-based remote access services with the Routing and Remote Access Service (RRAS). Both DirectAccess and RRAS can now be deployed on the same Edge server and managed by using Windows PowerShell commands and the Remote Access Microsoft Management Console (MMC).
DirectAccess enables remote users to securely access shared resources, Web sites, and applications on an internal network without connecting to a virtual private network (VPN). DirectAccess establishes bi-directional connectivity with an internal network every time a DirectAccess-enabled computer is connected to the Internet. Users never have to think about connecting to the internal network, and IT administrators can manage remote computers outside the office, even when the computers are not connected to the VPN.
https://technet.microsoft.com/en-us/library/dn636119.aspx
QUESTION 117
Your network contains an Active Directory forest named contoso.com.
The forest contains five domains.
You need to ensure that the CountryCode attribute is replicated to the global catalog.
What should you do?
A. Modify the configuration partition.
B. Create and modify an application partition.
C. Modify the schema partition.
D. Modify the domain partitions.
Answer: C
Explanation:
After an attributeSchema object is created, marking an additional attribute to replicate to the Global Catalog causes a full replication (also known as a “full sync”) of all objects to the Global Catalog.
https://support.microsoft.com/en-us/kb/248717
QUESTION 118
Your network contains an Active Directory domain named contoso.com.
All servers run Windows Server 2008 R2. All domain controllers are installed on physical servers.
The network contains several Hyper-V hosts.
The network contains a Microsoft System Center 2012 infrastructure.
You plan to use domain controller cloning to deploy several domain controllers that will run Windows Server 2012.
You need to recommend which changes must be made to the network infrastructure before you can use domain controller cloning.
What should you recommend?
A. Upgrade the domain controller that has the infrastructure master operations master role to Windows Server 2012. Install the Windows Deployment Services server role on a server that runs Windows Server 2012.
B. Upgrade the domain controller that has the PDC emulator operations master role to Windows Server 2012. Deploy a Hyper-V host that runs Windows Server 2012.
C. Upgrade a global catalog server to Windows Server 2012. Install the Windows Deployment Services server role on a server that runs Windows Server 2012.
D. Upgrade a global catalog server to Windows Server 2012.Deploy Virtual Machine Manager (VMM).
Answer: B
QUESTION 119
Your network contains 50 servers that run Windows Server 2003 and 50 servers that run Windows Server 2008.
You plan to implement Windows Server 2012 R2.
You need to create a report that includes the following information:
– The servers that run applications and services that can be moved to Windows Server 2012 R2
– The servers that have hardware that can run Windows Server 2012 R2
– The servers that are suitable to be converted to virtual machines hosted on Hyper-V hosts that run Windows Server 2012 R2
Solution: You install Windows Server 2012 R2 on a new server, and then you run Microsoft Deployment Toolkit (MDT) 2012.
Does this meet the goal?
A. Yes
B. No
Answer: B
QUESTION 120
Your network contains 50 servers that run Windows Server 2003 and 50 servers that run Windows Server 2008.
You plan to implement Windows Server 2012 R2.
You need to create a report that includes the following information:
– The servers that run applications and services that can be moved to Windows Server 2012 R2
– The servers that have hardware that can run Windows Server 2012 R2
– The servers that are suitable to be converted to virtual machines hosted on Hyper-V hosts that run Windows Server 2012 R2
Solution: You install Windows Server 2012 R2 on a new server, and then you run the Windows Server Migration Tools.
Does this meet the goal?
A. Yes
B. No
Answer: B
GreatExam offers the latest 70-413 PDF and VCE dumps with new version VCE player for free download, and the new 70-413 practice test ensures your exam 100% pass.