I’m currently studying for Microsoft exam 70-411. I do enjoy studying for exams. It’s hard, but it’s an excellent forcing function. I learn bits and pieces here and there now and then about this and that, but when I have an exam schedule for a set date, I have to study! And not only do I put in more hours, but I follow a more systematic approach. In this article, I’m going to share GreatExam braindumps in case you too are studying and this method works for you.
QUESTION 321
Your network contains one Active Directory domain named contoso.com.
From the Group Policy Management console, you view the details of a Group Policy object (GPO) named GPO1.
You need to ensure that the comments field of GPO1 contains a detailed description of GPO1.
What should you do?
A. From Active Directory Users and Computers, edit the properties of contoso.com/System/Policies/{229DCD27-9D98-ACC2-A6AE-ED765F065FF5}.
B. Open GPO1 in the Group Policy Management Editor, and then modify the properties of GPO1.
C. From Notepad, edit \\contoso.com\SYSVOL\ contoso.com\Policies\{229DCD27-9D98- ACC2-A6AE-ED765F065FF5}\gpt.ini.
D. From Group Policy Management, click View, and then click Customize.
Answer: B
Explanation:
Adding a comment to a Group Policy object Open the Group Policy Management Console. Expand the Group Policy Objects node.
Right-click the Group Policy object you want to comment and then click Edit.
In the console tree, right-click the name of the Group Policy object and then click Properties .
Click the Comment tab.
Type your comments in the Comment box.
Click OK
Reference: Comment a Group Policy Object
https://technet.microsoft.com/en-us/library/cc770974.aspx
QUESTION 322
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2008 R2.
You plan to test Windows Server 2012 R2 by using native-boot virtual hard disks (VHDs).
You have a Windows image file named file1.wim.
You need to add an image of a volume to file1.wim.
What should you do?
A. Run imagex.exe and specify the /append parameter.
B. Run imagex.exe and specify the /export parameter.
C. Run dism.exe and specify the /image parameter.
D. Run dism.exe and specify the /append-image parameter.
Answer: D
Explanation:
The Deployment Image Servicing and Management (DISM) tool is a command-line tool that enables the creation of Windows image (.wim) files for deployment in a manufacturing or corporate IT environment. The /Append-Image option appends a volume image to an existing .wim file allowing you to store many customized Windows images in a fraction of the space. When you combine two or more Windows image files into a single .wim, any files that are duplicated between the images are only stored once.
Incorrect:
Not A, Not B: Imagex has been retired and replaced by dism.
Reference: Append a Volume Image to an Existing Image Using DISM
https://technet.microsoft.com/en-us/library/hh824916.aspx
QUESTION 323
You have a server that runs Windows Server 2012 R2.
You have an offline image named Windows2012.vhd that contains an installation of Windows Server 2012 R2.
You plan to apply several updates to Windows2012.vhd.
You need to mount Wmdows2012.vhd to D:\Mount.
Which tool should you use?
A. Server Manager
B. Device Manager
C. Mountvol
D. Dism
Answer: D
Explanation:
You can use the Deployment Image Servicing and Management (DISM) tool to mount a Windows image from a WIM or VHD file.
Mounting an image maps the contents of the image to a directory so that you can service the image using DISM without booting into the image.
You can also perform common file operations, such as copying, pasting, and editing on a mounted image.
To apply packages and updates to a Windows Embedded Standard 7 image, we recommend creating a configuration set and then using Deployment Imaging Servicing and Management (DISM) to install that configuration set. Although DISM can be used to install individual updates to an image, this method carries some additional risks and is not recommended.
QUESTION 324
Your network contains a domain controller named DC1 that runs Windows Server 2012 R2.
You create a custom Data Collector Set (DCS) named DCS1.
You need to configure DCS1 to collect the following information:
– The amount of Active Directory data replicated between DC1 and the other
domain controllers
– The current values of several registry settings
Which two should you configure in DCS1? (Each correct answer presents part of the solution. Choose two.)
A. Event trace data
B. A performance counter alert
C. Configuration data collector
D. A performance counter
Answer: CD
Explanation:
Automatically run a program when the amount of total free disk space on Server1 drops below 10 percent of capacity.
You can also configure alerts to start applications and performance logs Log the current values of several registry settings.
System configuration information allows you to record the state of, and changes to, registry keys.
Total free disk space
Registry settings
Run a program on alert
Notes 2 :
The Windows Performance Monitor is an MMC snap-in (Microsoft Management Console), are provided in the tools for analyzing system performance. From a central console, you can monitor application and hardware performance in real-time, specify which data you want to collect in logs, define thresholds for alerts and automatic actions, generate reports, and view older performance data in several ways. With the Windows Performance Monitor data using data collector sets collected and logged may include performance indicators, event trace data, and system configuration information (registry key). Depending on the selected data collection types you various dialog boxes to add data files to your collection rate.
– Performance indicators provide data about the system performance.
– Performance indicators warnings allow you to run certain actions when exceeding or falling
below certain thresholds.
– To log registry settings, system configuration information can be recorded in reports. However,
you must know the exact key that you want to include in the Data Collector Set.
– Event trace data provide information about activities and system events are available.
– The relevant indicators for measuring the replication traffic of the Active Directory Domain
Services, see the performance object directory service. There are several indicators to measure
incoming and outgoing bytes / s.
http://technet.microsoft.com/en-us/library/cc766404.aspx
http://technet.microsoft.com/en-us/library/cc766404.aspx
QUESTION 325
Your corporate network includes an Active Directory Domain Services (AD DS) domain certbase.de named.
The domain contains a Windows Server 2012 R2 computer named Server3.
Server3 performs the role of Windows Deployment Services.
To use the Windows Deployment Services to distribute an image to a client computer that does not support PXE boot.
Which image type you will add Server3?
A. An install image
B. A boot image
C. A discover image
D. A capture image
Answer: C
Explanation:
The main image types used in Windows Deployment Services are installation and boot images.
Install images
Install images are the operating system images that you deploy to the client computer. You can use the default install image (install.wim) located on the DVD of Windows Vista or Windows Server 2008 in the \ Sources directory.
You can also create custom install images from reference computers and deploy them to client computers. First, you boot a computer (which has been prepared with Sysprep) into a capture image. Then the capture image an install image of the computer is created.
Boot images
Boot images are the images with which you start a client computer before installing the operating system image. The boot image presents a boot menu that contains the images that users can install on their computers.
These images contain Windows PE 2.0 and the Windows Deployment Services client. You can use the default boot image included in the \ Sources directory of the Windows Server 2008 installation media (boot.wim).
This file must be only in advanced scenarios (for example, if you must add the image driver) to be changed. Important Only use the Boot.wim file on the Windows Server 2008 DVD.
If you boot.wim file to use on the Windows Vista DVD, you can not use all the functionality of Windows Deployment Services (for example, multicasting). There are also two image types that you can create from boot images:. Capture images and discover images.
Capture Images
Capture Images are boot images that allow the utility starts to record the Windows Deployment Services in place of the setup. If a reference computer (which has been prepared with Sysprep) start with a capture image, an install image of the reference computer is created and saved as a WIM file with an assistant. You can also create a medium (eg, CD, DVD or USB drive) that contains a capture image, and then boot a computer to the media. After you create the install image, you can use the image for PXE boot deployment Add the server. These images provide an alternative to command-line tool ImageX.exe.
Discover images
Discover images search images are boot images, which is enforced by that Setup.exe in Windows Deployment Services mode is started. Subsequently, a Windows Deployment Services server will be searched.
These images are typically used to deploy images to computers that are not configured for PXE or that are in networks where PXE is not allowed. If you create a discover image and apply it to the medium (eg, CD, DVD or Save USB drive), you can then boot a computer to the media.
The discover image on the media of the Windows Deployment Services server will be searched. The installation image is provided by the server for the computer. You can configure discover images so that a specific Windows Deployment Services server is used as a target. This means that you can create a discover image when a plurality of servers in your environment for each server and then can name each based on the name of the server.
QUESTION 326
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named dcl.contoso.com.
You discover that the Default Domain Policy Group Policy objects (GPOs) and the Default Domain Controllers Policy GPOs were deleted.
You need to recover the Default Domain Policy and the Default Domain Controllers Policy GPOs. What should you run?
A. dcgpofix.exe /target:domain
B. gpfixup.exe /dc:dc1.contoso.com
C. dcgpofix.exe /target:both
D. gptixup.exe /oldnb:contoso /newnb:dc1
Answer: C
Explanation:
This command-line tool Dcgpofix there since Windows Server 2003. It allows the rebuild of the two default Group Policy objects (GPOs) Default Domain Policy (DDP) and Default Domain Controllers Policy (ddCDP) or is it the two GPOs to their default settings if you exist.
Parameter /Target specifies what you want to restore the two default GPOs. Here the self-explanatory values are domain, DC or Both possible.
The command-line utility GPFixup resolves issues with references to domain names, which can possibly occur during a domain rename.
QUESTION 327
Your network contains an Active Directory domain named contoso.com.
The domain contains more than 100 Group Policy objects (GPOs).
Currently, there are no enforced GPOs.
You need to provide an Administrator named Admin1 with the ability to create GPOs in the domain. The solution must not provide Sarah with the ability to link GPOs.
What should you use?
A. dcgpofix
B. Get-GPOReport
C. Gpfixup
D. Gpresult
E. Gptedit.msc
F. Import-GPO
G. Restore-GPO
H. Set-GPInheritance
I. Set-GPLink
J. Set-GPPermission
K. Gpupdate
L. Add-ADGroupMember
Answer: L
Explanation:
We can run the add-ADGroupMember use and Sarah in the Default Domain Group Policy Creator Owners record.
Members of this group can create and modify GPOs, but do not link.
QUESTION 328
Your network contains an Active Directory domain named contoso.com.
All client computers run Windows 8 Pro.
You have a Group Policy object (GPO) named GP1. GP1 is linked to the domain.
GP1 contains the Windows Internet Explorer 10 and 11 Internet Settings.
The settings are shown in the exhibit.
Users report that when they open Windows Internet Explorer, the home page is NOT set to http:// www.contoso.com.
You need to ensure that the home page is set to http://www.contoso.com the next time users log on to the domain.
What should you do?
A. On each client computer, run gpupdate.exe.
B. Open the Internet Explorer 10 and 11 Internet Settings, and then press F5.
C. Open the Internet Explorer 10 and 11 Internet Settings, and then modify the Tabs settings.
D. On each client computer, run Invoke-GPupdate.
Answer: B
Explanation:
The Section Home on the tab General is marked with a red dashed line.
This indicates that the setting has the status of “not configured”.
If you press while the dialog box is open, the F5 key is changing the red dotted line in a solid green line, which “activates” corresponds to the policy status.
Configure the following key combinations the status of the settings of the current tab:
F5 – All settings activated (green)
F6 – A setting is enabled (green)
F7 – A setting is not configured (red)
F8 – All settings are not activated (red)
QUESTION 329
Your network contains an Active Directory domain named contoso.com.
The domain contains 30 organizational units (OUs).
You need to ensure that a user named User1 can link Group Policy Objects (GPOs) in the domain.
What should you do?
A. From the Active Directory Users and Computers, add User1 to the Network Configuration Operators group.
B. From the Group Policies Management, click the contoso.com node and modify the Delegation settings.
C. From the Group Policies Management, click the Group policy Objects node and modify the Delegation settings.
D. From the Active Directory Users and Computers, add User1 to the Group Policy Creator Owners group.
Answer: B
Explanation:
In addition to the administrators of a domain by default, members of the Group Policy Creator Owners group the right to create group policies. If you want to enable users or groups to itself to create GPOs, then there is a path on their inclusion in the Group Policy Creator Owners group.
However, since the introduction of the Group Policy Management, there are other and more granular ways to delegate rights to manage GPOs. Thus, other groups or even individual users can now be equipped with these privileges. For this purpose you open the Group Policy Objects folder below the respective domain. Under the tab delegation is a list of all the groups and users who have the right to create GPOs. The button can add additional users are granted this privilege.
No matter how a user gets the right to create GPOs to, he may subsequently only edit or delete, which he himself has created those. Denied him thus remains the possibility to change already existing group policies or generally to link GPOs to an OU. For these tasks, users must be authorized separately.
The right to link GPOs can a user, as described in answer B, be granted.
QUESTION 330
Your network contains an Active Directory domain named contoso.com.
All client computers run Windows 8.
Your company has users who work from home. Some of the home users have desktop computers. Other home users have laptop computers.
All of the computers are joined to the domain.
All of the computer accounts are members of a group named Group1.
Currently, the home users access the corporate network by using a PPTP VPN.
You implement DirectAccess by using the default configuration and you specify Group1 as the DirectAccess client group.
The home users who have desktop computers report that they cannot use DirectAccess to access the corporate network.
The home users who have laptop computers report that they can use DirectAccess to access the corporate network.
You need to ensure that the home users who have desktop computers can access the network by using DirectAccess.
What should you modify?
A. The security settings of the computer accounts for the desktop computers
B. The membership of the RAS and IAS Servers group
C. The WMI filter for Direct Access Client Settings GPO
D. The conditions of the Connections to Microsoft Routing and Remote Access server policy
Answer: C
Explanation:
By default, the DirectAccess wizard DirectAccess prepared by applying a WMI filter on the GPO for the client settings for all laptops and notebook computers in the domain.
To apply the settings of the GPOs for DirectAccess clients on all the group CBRemotecomputer computer, we need to change or remove the WMI filter.
QUESTION 331
You have a Direct Access Server named Server1 running Server 2012.
You need to add prevent users from accessing websites from an Internet connection.
What should you configure?
A. Split Tunneling
B. Security Groups
C. Force Tunneling
D. Network Settings
Answer: C
Explanation:
If Direct Access is configured for Tunnelerzwingung, compounds of the DirectAccess client to the internal network and the Internet via the remote access server are routed. In the corporate network a proxy or a web filter can then be used, which blocks access to certain sites.
By default, the option is not enabled Tunnelerzwingung use.
The figure shows the default setting in the wizard for DirectAccess configuration:
QUESTION 332
Your network contains an Active Directory domain named contoso.com. The domain contains three domain controllers. The domain controllers are configured as shown in the following table.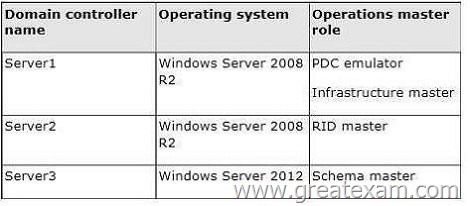
You are creating a Distributed File System (DFS) namespace as shown in the exhibit.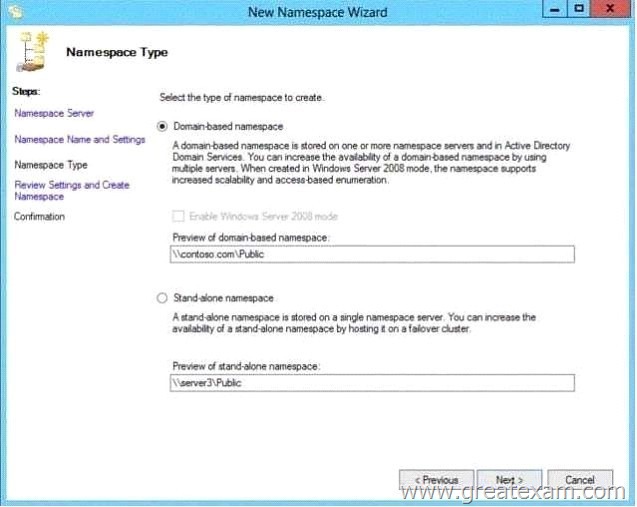
You need to identify which configuration prevents you from creating a DFS namespace in Windows Server 2008 mode.
Which configuration should you identify?
A. The location of the PDC emulator role
B. The functional level of the domain
C. The operating system on Server1 and Server3
D. The location of the RID master role
Answer: B
Explanation:
With DFS Namespaces (Distributed File System, Distributed File System) and the DFS Replication is simplified, enabling highly available access to files, load balancing and WAN-friendly replication. In the operating system Windows Server 2003 R2 Microsoft DFS Namespaces has (formerly known as DFS) revised and renamed, the DFS Management snap-in through the DFS Management snap-in replaces and introduced the new DFS Replication feature. In the operating system Windows Server 2008 Windows Server 2008 mode for domain-based namespaces as well as a number of improvements in terms of usability and performance have been added. With the DFS technologies WAN-friendly (Wide Area Network) replication and simplified, highly available access to geographically Distributed files allows. DFS includes these two technologies:
DFS Namespaces Using DFS Namespaces You can shared folders located on different servers, are grouped into one or more logically structured namespaces. Each namespace is displayed to users as a single shared folder with a series of subfolders. With this structure, the availability is increased, and for user connections to shared folders on the same Active Directory Domain Services site are automatically prepared, if it is available. Users are therefore not routed over WAN links.
DFS Replication DFS Replication is an efficient replication engine with multiple masters, with the folders between servers via network connections with limited bandwidth can be continuously synchronized. Thus, the FRS will File Replication Service (FRS) replaces a replication module for DFS Namespaces and for replication of the AD DS SYSVOL folder in domains that use the Windows Server 2008 domain functional level is used.
Domain-based namespaces in Windows Server 2008 mode
in Windows Server 2008 can domain-based namespaces in Windows Server 2008 mode are created. This support for access-based enumeration and increased scalability is activated. The 2000 Server introduced in Windows domain-based namespace is now referred to as “domain-based namespace (Windows 2000 Server mode).” To use the Windows Server 2008 mode, the domain and the domain-based namespace must meet the following minimum requirements:
For the domain, the Windows Server 2008 domain functional level is used.
On all namespace servers running Windows Server of 2008.
QUESTION 333
On the DFS replication your receive a wrap error on the sysvol on domain controller 4.
Which 3 steps should you do to recover this error in the correct order?
A. Stop FSR
B. Start FSR
C. Edit the computer object in AD
D. Edit the registry
E. Stop DFSR
F. Start DFRS
Answer: ABD
QUESTION 12
Your network contains an Active Directory domain named contoso.com. The domain functional level is Windows Server 2008. All domain controllers run Windows Server 2008 R2.
The domain contains a file server named Server1 that runs Windows Server 2012. Server1 has a BitLocker Drive Encryption (BitLocker)-encrypted drive.
Server1 uses a Trusted Platform Module (TPM) chip.
You enable the Turn on TPM backup to Active Directory Domain Services policy setting by using a Group Policy object (GPO).
You need to ensure that you can back up the BitLocker recovery information to Active Directory.
What should you do?
A. Raise the forest functional level to Windows Server 2008 R2.
B. Enable the Configure the level of TPM owner authorization information available to the operating system policy setting and set the Operating system managed TPM authentication level to None.
C. Add a BitLocker data recovery agent.
D. Import the TpmSchemaExtension.ldf and TpmSchemaExtensionACLChanges.ldf schema extensions to the Active Directory schema.
Answer: D
QUESTION 334
Your network contains an Active Directory domain named contoso.com.
The domain contains 2 WSUS servers, ServerA and ServerB.
ServerB is a replica server of ServerA.
You need to configure WSUS to report data from SERVERB to SERVERA.
What should you configure?
A. Update Reports
B. Synchronization
C. Computer Groups
D. Reporting Rollup
Answer: D
QUESTION 335
You are an admin. You have wsus with 2 sites which contain computers.
You want to have the ability to update the computers per site or together.
Which 3 steps do you do?
A. Create computer groups in wsus
B. Create synchronization options
C. Create GPO and configure updates
D. Under Tasks, click Synchronize now
Answer: ABC
QUESTION 336
Which of the options should you configure for a WDS pre-staged computer name?
You should select 2 of the 4 check boxes.
A. GUID o MAC-address preceding with nulls
B. WdsClientUnattend
C. Give the minimum required permission to a user who wants to promote a RODC.
D. ReferralServer
Answer: AC
QUESTION 337
You work as a network administrator at Lead2pass.com.
Lead2pass.com has an Active Directory Domain Services (AD DS) domain name Lead2pass.com.
All servers in the Lead2pass.com domain have Microsoft Windows Server 2012 R2 installed.
The computer accounts for all file servers are located in an organizational unit (OU) named DataOU. You are required to track user access to shared folders on the file servers.
Which of the following actions should you consider?
A. You should configure auditing of Account Logon events for the DataOU.
B. You should configure auditing of Object Access events for the DataOU.
C. You should configure auditing of Global Object Access Auditing events for the DataOU.
D. You should configure auditing of Directory Service Access events for the DataOU.
E. You should configure auditing of Privilege Use events for the DataOU.
Answer: B
QUESTION 338
You have installed Routing and Remote Access on Server1.
What should you configure next to use it as a NAT server?
A. Add New Interface
B. Create Static Route
C. Configure the IPv4 DHCP Relay Agent
D. Configure the IPv6 DHCP Relay Agent
Answer: A
QUESTION 339
Force an authoritative and non-authoritative synchronization for DFSR-replicated SYSVOL
A. dfsgui.msc
B. ultrasound
C. rplmon
D. frsutil
Answer: C
QUESTION 340
How to give the minimum required permission to a user who wants to promote a RODC.
A. member of the Domain Admins group
B. allowed to attach the server to the RODC computer account
C. Local admin
D. organization admin
Answer: BC
If you want to prepare for 70-411 exam in shortest time, with minimum effort but for most effective result, you can use GreatExam 70-411 practice test which simulates the actual testing environment and allows you to focus on various sections of 70-411 exam. Best of luck!