70-411 exam questions and answers provided by GreatExam will guarantee you pass 70-411 exam, because GreatExam is the top IT Certification study training materials vendor. Many candidates have passed exam with the help of GreatExam. We offer the latest 70-411 PDF and VCE dumps with new version VCE player for free download, you can pass the exam beyond any doubt.
QUESTION 201
Hotspot Question
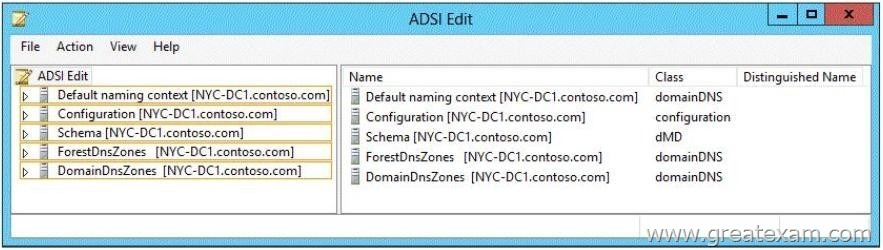
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. The contoso.com zone is Active Directory-integrated and configured to replicate to all of the domain controllers in the contoso.com domain. Server1 has a DNS record in the contoso.com zone.
You need to verify when the DNS record for Server1 was last updated.
In which Active Directory partition should you view the DNS record of Server1?
To answer, select the appropriate Active Directory partition in the answer area.
Answer:
Explanation:
From the task text shows that the zone data is replicated to all domain controllers in the domain contoso.com. This corresponds to the replication scope for Windows 2000 compatibility.
The partitions DomainDNSZones and ForestDNSZones were only introduced with Windows Server 2003. On Windows 2000 Server DNS zone data stored in the domain partition and replicated to all domain controllers (not only domain controllers with the DNS server role).
QUESTION 202
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 has the Windows Server Update Services (WSUS) server role installed. WSUS is configured to use a Windows Internal Database. Server2 has Microsoft SQL Server 2008 R2 Standard deployed.
You detach the SUSDB database from Server1 and attach the database to Server2.
You need to ensure that Windows Deployment Services (WDS) on Server1 uses the database hosted on Server2.
What should you do on Server1?
A. Configure an ODBC file data source.
B. Run the wsusutil command.
C. Edit the registry.
D. Configure an ODBC system data source.
Answer: C
Explanation:
Find the following key:
HKLM\SOFTWARE\Microsoft\UpdateServices\Server\Setup\SqlServerName. In the Value data box, type [BEName]\[InstanceName], and then click OK. If the instance name is the default instance, type [BEName].
Find the following key: HKLM\Software\Microsoft\Update Services\Server\Setup\wYukonInstalled. In the Value box, type 0, and then click OK. http://technet.microsoft.com/en-us/library/cc708558(WS.10).aspx
QUESTION 203
Your network contains an Active Directory forest named contoso.com. The functional level of the forest is Windows Server 2008 R2. All of the user accounts in the marketing department are members of a group named Contoso\MarketingUsers. All of the computer accounts in the marketing department are members of a group named Contoso\MarketingComputers.
A domain user named User1 is a member of the Contoso\MarketingUsers group.
A computer named Computer1 is a member of the Contoso\MarketingComputers group.
You have five Password Settings objects (PSOs).
The PSOs are defined as shown in the following table.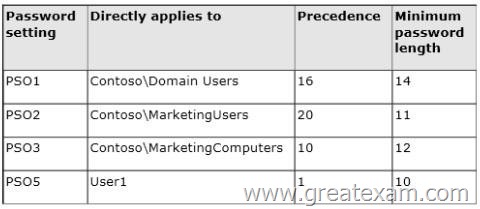
When User1 logs on to Computer1 and attempts to change her password, she receives an error message indicating that her password is too short.
You need to tell User1 what her minimum password length is.
What should you tell User1?
A. 10
B. 11
C. 12
D. 14
Answer: A
Explanation:
Let’s take the G_ITAdmins group and apply two PSOs, one with precedence of 10 and one with precedence of 5.
The PSO with precedence of 5 will win, because a lower precedence value is a higher precedence.
This makes sense if you are just using groups and apply the PSO to the group level.
But what happens if you apply a PSO to the group G_ITAdmins (Sally Smith is still a member) and you apply a PSO directly to Sally Smith?
Let’s take the G_ITAdmins group again, where Sally Smith is a member, and apply a PSO with a precedence of 10.
Create another PSO with a precedence of 15 and apply this PSO directly to the user Sally Smith.
The PSO directly applied to Sally will win, although the precedence value is higher.
The way that the PSO applied is determined is as follows:
A PSO that is linked directly to the user object is the resultant PSO. If no PSO is linked to the user object, the global security group memberships of the user – and all PSOs that are applicable to the user based on those global group memberships—are compared. The PSO with the lowest precedence value is the resultant PSO.
https://technet.microsoft.com/en-us/library/cc770394%28v=ws.10%29.aspx
QUESTION 204
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Remote Access server role installed.
You log on to Server1 by using a user account named User2.
From the Remote Access Management Console, you run the Getting Started Wizard and you receive a warning message as shown in the exhibit. (Click the Exhibit button.)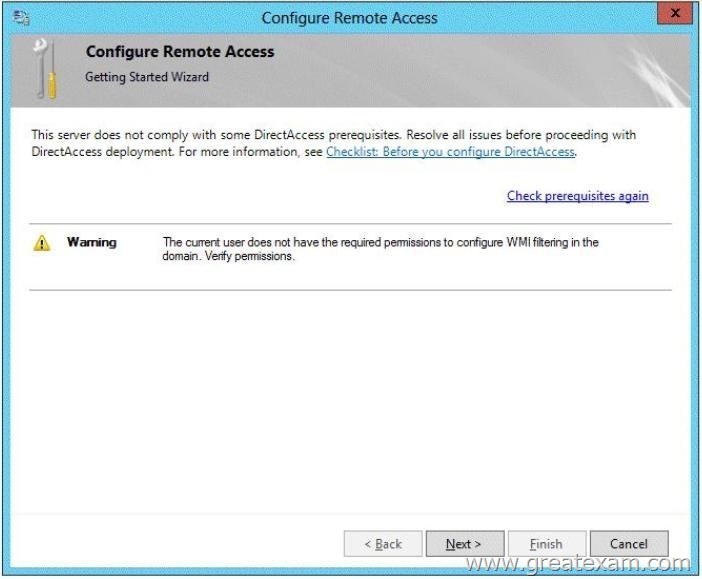
You need to ensure that you can configure DirectAccess successfully.
The solution must minimize the number of permissions assigned to User2.
To which group should you add User2?
A. Enterprise Admins
B. Administrators
C. Server Operators
D. Account Operators
Answer: B
Explanation:
You must have privileges to create WMI filters in the domain in which you want to create the filter. Permissions can be changed by adding a user to the Administrators group.
Administrators (A built-in group)
After the initial installation of the operating system, the only member of the group is the Administrator account. When a computer joins a domain, the Domain Admins group is added to the Administrators group. When a server becomes a domain controller, the Enterprise Admins group also is added to the Administrators group. The Administrators group has built-in capabilities that give its members full control over the system.
The group is the default owner of any object that is created by a member of the group.
This example logs in as a test user who is not a domain user or an administrator on the server. This results in the error specifying that DA can only be configured by a user with local administrator permissions.
http://technet.microsoft.com/en-us/library/cc780416(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc775497(v=ws.10).aspx
QUESTION 205
Your company has a main office and a branch office. The network contains an Active Directory domain named contoso.com. The main office contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 is a DNS server and hosts a primary zone for contoso.com.
The branch office contains a member server named Server1 that runs Windows Server 2012 R2. Server1 is a DNS server and hosts a secondary zone for contoso.com. The main office connects to the branch office by using an unreliable WAN link.
You need to ensure that Server1 can resolve names in contoso.com if the WAN link in unavailable for three days.
Which setting should you modify in the start of authority (SOA) record?
A. Retry interval
B. Minimum (default) TTL
C. Refresh interval
D. Expires after
Answer: D
Explanation:
Refresh interval. Used to determine how often other DNS servers that load and host the zone must attempt to renew the zone.
Retry interval. Used to determine how often other DNS servers that load and host the zone are to retry a request for update of the zone each time that the refresh interval occurs. Expire interval. Used by other DNS servers that are configured to load and host the zone to determine when zone data expires if it is not renewed.
QUESTION 206
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Network Policy and Access Services server role installed.
You plan to deploy 802.1x authentication to secure the wireless network.
You need to identify which Network Policy Server (NPS) authentication method supports certificate-based mutual authentication for the 802.lx deployment.
Which authentication method should you identify?
A. PEAP-MS-CHAP v2
B. MS-CHAP v2
C. EAP-TLS
D. MS-CHAP
Answer: C
Explanation:
802. 1X uses EAP, EAP-TLS, EAP-MS-CHAP v2, and PEAP authentication methods:
EAP (Extensible Authentication Protocol) uses an arbitrary authentication method, such as certificates, smart cards, or credentials.
EAP-TLS (EAP-Transport Layer Security) is an EAP type that is used in certificatebased security environments, and it provides the strongest authentication and key determination method.
EAP-MS-CHAP v2 (EAP-Microsoft Challenge Handshake Authentication Protocol version 2) is a mutual authentication method that supports password-based user or computer authentication.
PEAP (Protected EAP) is an authentication method that uses TLS to enhance the security of other EAP authentication protocols.
QUESTION 207
Your network contains an Active Directory domain named contoso.com. AH servers run Windows Server 2012 R2. The domain contains a server named Server1.
You install the Windows PowerShell Web Access gateway on Server1.
You need to provide administrators with the ability to manage the servers in the domain by using the Windows PowerShell Web Access gateway.
Which two cmdlets should you run on Server1?
(Each correct answer presents part of the solution. Choose two.)
A. Set-WSManQuickConfig
B. Set-WSManInstance
C. Add-PswaAuthorizationRule
D. Set-BCAuthentication
E. Install-Pswa Web Application
Answer: CE
Explanation:
Windows PowerShell Web Access is a new feature in Windows Server 2012 that acts as a Windows PowerShell Gateway and the web-based Windows PowerShell console is provided, which is aligned on a remote computer. In order to run IT specialists Windows PowerShell commands and scripts on a Windows PowerShell console in a Web browser without having Windows PowerShell, remote management software or browser plug-ins must be installed on the client device. To run the web-based Windows PowerShell console a properly configured Windows PowerShell Web Access gateway and a browser on the client device is only necessary that supports JavaScript and cookies accepted.
Examples of client devices include laptops, privately used personal computers, borrowed computers, tablet PCs, Webkiosks, computers that are not Windows-based operating system is running, and browsers on cell phones. IT professionals can use devices that have access to an internet connection and a web browser perform key administrative tasks on Windows-based remote servers. After the successful setup and configuration of the gateway, users can access PowerShell console with a Web browser on a Windows.
After searching the protected Windows PowerShell Web Access site open, you can run a web-based Windows PowerShell console after successful authentication. The setup and configuration of Windows PowerShell Web Access involves three steps:
Step 1: Install Windows PowerShell Web Access
Step 2: Configuring the Gateway
Step 3: Configuring authorization rules and site security
QUESTION 208
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
All domain controllers run Windows Server 2012 R2.
The domain contains an organizational unit (OU) named OU1.
OU1 contains an OU named OU2. OU2 contains a user named User1.
User1 is the member of a group named Group1.
Group1 is in the Users container.
You create five Group Policy objects (GPO).
The GPOs are configured as shown in the following table.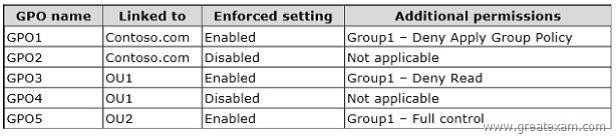
You need to identify which three GPOs will be applied to User1 and in which order the GPOs will be applied to User1.
Which three GPOs should you identify in sequence?
To answer, move the appropriate three GPOs from the list of GPOs to the answer area and arrange them in the correct order.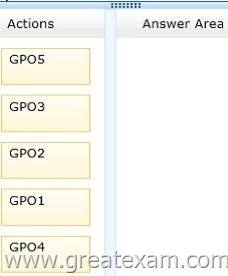
Answer:
Explanation:
Basically determines the order in which the GPOs are applied by Group Policy, the ranking. The default order is local, site, domain, organizational unit and subordinate organizational units (OU LSD). Therefore GPOs have in child OUs overrides associated with parent OUs GPOs.
This in turn take precedence over the domain linked GPOs, which take precedence over the site linked GPOs. Direction for use, or LSD-OU (LSDOU)
1. Local Policy
2. GPOs that are linked to the site
3. GPOs that are linked to the domain
4. GPOs that are linked to organizational units (from the parent OU to subordinate)
The Standardreiehnfolge processing can be set by forcing a Group Policy object or by disabling the inheritance of a GPO repealed. Enforced When a GPO enforced it will put at the end of the processing sequence. If more than one GPO to “forced” option is enabled, the GPOs are applied in reverse default order (L-OU-DS).
In this way ensures that the settings of Domain Admins will not be overwritten by forcing the settings of a Delegated Administrator at a subordinate level. If several enforced GPO objects linked on the same level as, shall be the highest priority by (the sorted upwards). Inheritance disable The above the OU linked GPOs are not inherited or blocked.
Is activated by a higher-level object “forced”, so the inheritance can not be prevented. Thus, the Domain Administrator can always prevail with its settings. For taking over the settings of a GPO a Sicherheitrsprinzipal required permissions Read and Apply Group Policy. If the security principal denied these rights, the GPO does not apply.
QUESTION 209
Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has two network adapters and is located in a perimeter network.
You need to install the RIP version 2 routing protocol on Server1.
Which node should you use to add the RIP version 2 routing protocol?
To answer, select the appropriate node in the answer area.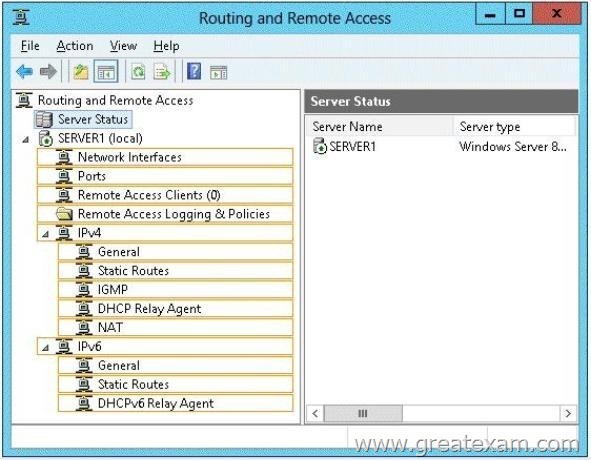
Answer: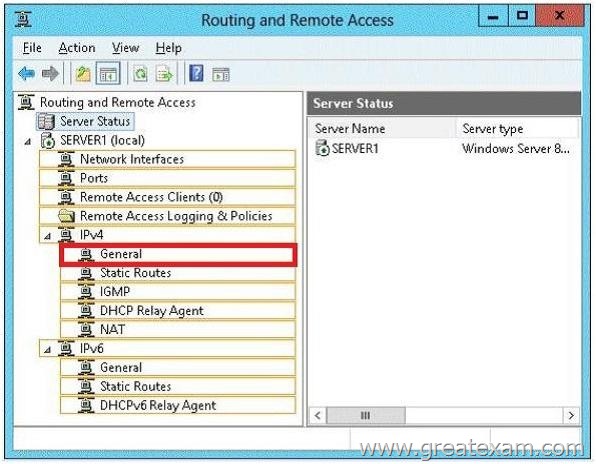
QUESTION 210
Hotspot Question
Your network contains an Active Directory domain named contoso.com. All DNS servers host a DNS zone named adatum.com. The adatum.com zone is not Active Directory-integrated. An administrator modifies the start of authority (SOA) record for the adatum.com zone. After the modification, you discover that when you add or modify DNS records in the adatum.com zone, the changes are not transferred to the DNS servers that host secondary copies of the adatum.com zone.
You need to ensure that the records are transferred to all the copies of the adatum.com zone. What should you modify in the SOA record for the adatum.com zone?
To answer, select the appropriate setting in the answer area.
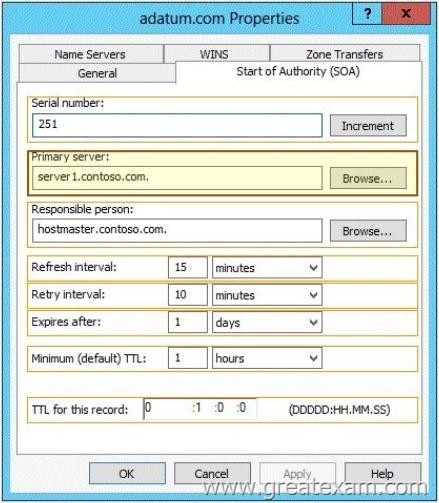
Answer: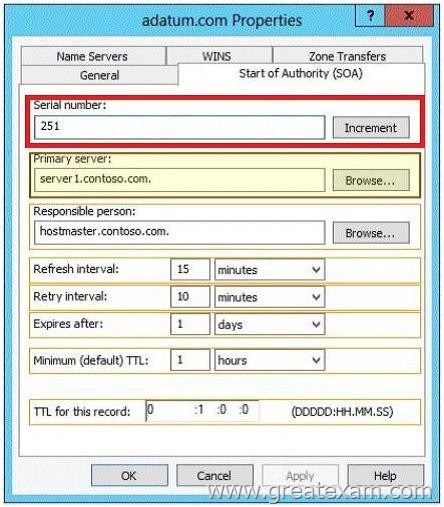
Explanation:
By increasing the serial number is initiated for an immediate transfer of zone data to all secondary servers. The SOA resource record contains the following information:
Serial number The revision number of the zone file. If changes the number is increased. By increasing the serial number change to any secondary DNS servers are distributed.
Primary Server – The host on which the file was created.
Responsible Person – The E-mail address of the person responsible for managing the zone file of the domain. Note that in the e-mail name instead of the symbol “@” a “.” is used.
Update time – The time waiting for a secondary DNS server before querying the SOA record of the primary DNS server for changes. If the update time expires, the secondary DNS server from the primary server requests a copy of the current SOA record. The primary DNS server complies with this request. The secondary DNS server compares the serial number of the current SOA record of the primary DNS server with the serial number in its own SOA record. If these numbers do not match, calls the secondary DNS server of the primary DNS server to a zone transfer. The default value is 3,600.
Repetition Time – The time waiting for a secondary server, before retrying a failed zone transfer is repeated. Usually, the repetition time is shorter than the update time. The default value is 600th
Elapsed time – The time in which a secondary server continues to try to perform a zone transfer. When this time expires prior to a successful zone transfer, the secondary server verrwirft its zone file. This has the result that the secondary server stops responding to queries when it considers its data too old and no longer reliable. The default value is 86,400.
Time to live (TTL) – The minimum value of Live (TTL) value applies to all resource records of the zone file. This value is contained in the answers to queries to DNS clients to inform about how long they should keep the data in the cache. The default value is 3,600.
QUESTION 211
Your network contains an Active Directory domain named contoso. com.
All domain controllers run either Windows Server 2008 or Windows Server 2008 R2.
You deploy a new domain controller named DC1 that runs Windows Server 2012 R2.
You log on to DC1 by using an account that is a member of the Domain Admins group.
You discover that you cannot create Password Settings objects (PSOs) by using Active Directory Administrative Center.
You need to ensure that you can create PSOs from Active Directory Administrative Center.
What should you do?
A. Modify the membership of the Group Policy Creator Owners group.
B. Transfer the PDC emulator operations master role to DC1.
C. Upgrade all of the domain controllers that run Window Server 2008.
D. Raise the functional level of the domain.
Answer: D
Explanation:
Fine-grained password policies allow you to specify multiple password policies within a single domain so that you can apply different restrictions for password and account lockout policies to different sets of users in a domain. To use a fine-grained password policy, your domain functional level must be at least Windows Server 2008. To enable fine-grained password policies, you first create a Password Settings Object (PSO).
You then configure the same settings that you configure for the password and account lockout policies.
You can create and apply PSOs in the Windows Server 2012 environment by using the Active Directory Administrative Center (ADAC) or Windows PowerShell.
Step 1: Create a PSO
Applies To: Windows Server 2008, Windows Server 2008 R2
http://technet.microsoft.com/en-us//library/cc754461%28v=ws.10%29.aspx
QUESTION 212
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains 200 Group Policy objects (GPOs) and 100 WMI filters. An administrator named Admin1 must be able to create new WMI filters and edit all of the existing WMI filters from the Group Policy Management Console (GPMC).
You need to delegate the required permissions to Admin1.
The solution must minimize the number of permissions assigned to Admin1.
What should you do?
A. From Group Policy Management, assign Full control to Admin1 for the WMI Filters container.
B. From Active Directory Users and Computers, add Admin1 to the Domain Admins group.
C. From Group Policy Management, assign Creator Owner to Admin1 for the WMI Filters container.
D. From Active Directory Users and Computers, add Admin1 to the WinRMRemoteWMIUsers__group.
Answer: A
Explanation:
Users with Full control permissions can create and control all WMI filters in the domain,
including WMI filters created by others.
Users with Creator owner permissions can create WMI filters, but can only control WMI filters that they create.
http://technet.microsoft.com/en-us/library/cc757429(v=ws.10).aspx
Note: Another similar question say “An administrator named Admin1 must be able to add new WMI filters from the Group Policy Management Console (GPMC).”, then you should choose “Users with Creator owner permissions”.
QUESTION 213
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Windows Server Update Services server role installed. All client computers are configured to download updates from Server1.
You have a Group Policy object (GPO) named GPO1 that is linked to an organizational unit (OU) named Sales_OU.
You need to ensure that all of the computers in Sales_OU are added to a Windows Server Update Services (WSUS) computer group named SalesComputers.
Which setting should you configure in the GPO?
To answer, select the appropriate setting in the answer area.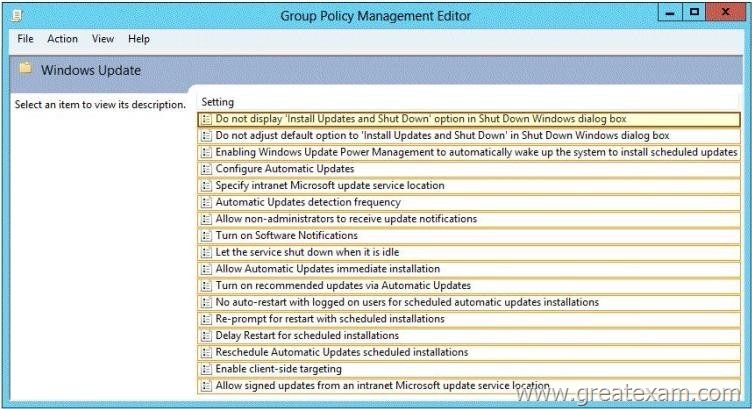
Answer: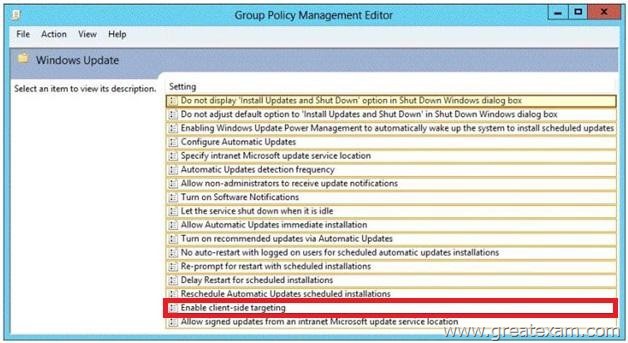
QUESTION 214
Your network contains three Network Policy Server (NPS) servers named NPS1, NPS2, and NPS3. NPS1 is configured as a RADIUS proxy that forwards connection requests to a remote RADIUS server group named Group1.
You need to ensure that NPS2 receives connection requests.
NPS3 must only receive connection requests if NPS2 is unavailable.
How should you configure Group1?
A. Change the Weight of NPS2 to 10.
B. Change the Weight of NPS3 to 10.
C. Change the Priority of NPS2 to 10.
D. Change the Priority of NPS3 to 10.
Answer: D
Explanation:
Priority specifies the order of importance of the RADIUS server to the NPS proxy server. Priority level must be assigned a value that is an integer, such as 1, 2, or 3. The lower the number, the higher priority the NPS proxy gives to the RADIUS server. For example, if the RADIUS server is assigned the highest priority of 1, the NPS proxy sends connection requests to the RADIUS server first; if servers with priority 1 are not available, NPS then sends connection requests to RADIUS servers with priority 2, and so on. You can assign the same priority to multiple RADIUS servers, and then use the Weight setting to load balance between them.
QUESTION 215
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains three servers named Server2, Server3, and Server4.
Server2 and Server4 host a Distributed File System (DFS) namespace named Namespace1.
You open the DFS Management console as shown in the exhibit. (Click the Exhibit button.)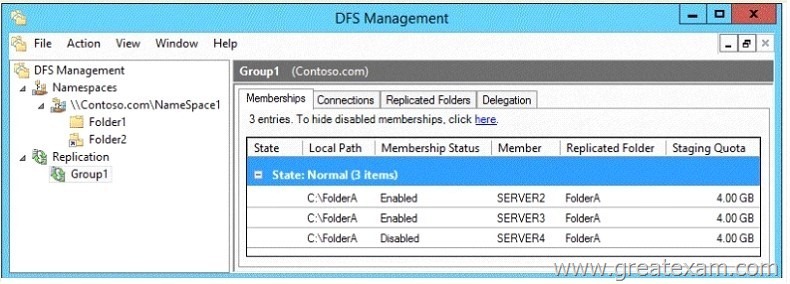
To answer, complete each statement according to the information presented in the exhibit.
Each correct selection is worth one point.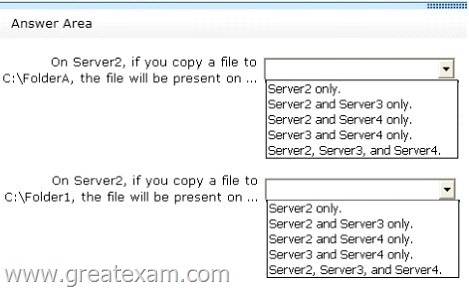
Answer: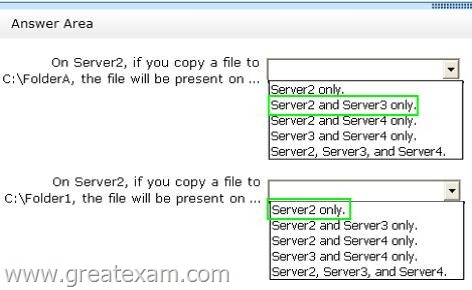
Explanation:
In Folder1 is a folder without folder targets. This can be seen on the icon of the folder. For Folder1 therefore may also be configured not replication. In the shown memberships of the replication group, it must therefore be the replication of the folder targets of folder2.
The replication of the target folder on Server4 is disabled. Files that are copied to Server2 Server3 or in folder2 are therefore not replicated to Server4.
For the physical directory C: \ folder1 is neither a target nor DFS folder DFS Replication is configured.
QUESTION 216
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2.
You plan to use fine-grained password policies to customize the password policy settings of contoso.com.
You need to identify to which Active Directory object types you can directly apply the fine-grained password policies.
Which two object types should you identify?
(Each correct answer presents part of the solution. Choose two.)
A. Domain local groups
B. Computers
C. Universal groups
D. Global groups
E. Users
Answer: DE
Explanation:
First off, your domain functional level must be at Windows Server 2008. Second, Fine-grained password policies ONLY apply to user objects, and global security groups. Linking them to universal or domain local groups is ineffective. I know what you’re thinking, what about OU’s? Nope, Fine-grained password policy cannot be applied to an organizational unit (OU) directly.
The third thing to keep in mind is, by default only members of the Domain Admins group can set fine-grained password policies. However, you can delegate this ability to other users if needed.
Fine-grained password policies apply only to user objects (or inetOrgPerson objects if they are used instead of user objects) and global security groups.
You can apply Password Settings objects (PSOs) to users or global security groups:
http://technet.microsoft.com/en-us/library/cc731589%28v=ws.10%29.aspx http://technet.microsoft.com/en-us/library/cc731589%28v=ws.10%29.aspx http://technet.microsoft.com/en-us/library/cc770848%28v=ws.10%29.aspx http://www.brandonlawson.com/active-directory/creating-fine-grained-password-policies/
QUESTION 217
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. All client computers run Windows 8 Enterprise. DC1 contains a Group Policy object (GPO) named GPO1.
You need to update the PATH variable on all of the client computers.
Which Group Policy preference should you configure?
A. Ini Files
B. Services
C. Environment
D. Data Sources
Answer: C
Explanation:
Environment Variable preference items allow you to create, update, replace, and delete user and system environment variables or semicolon-delimited segments of the PATH variable. Before you create an Environment Variable preference item, you should review the behavior of each type of action possible with this extension.
QUESTION 218
Your network has a router named Router1 that provides access to the Internet.
You have a server named Server1 that runs Windows Server 2012 R2. Server1 to use Router1 as the default gateway. A new router named Router2 is added to the network. Router2 provides access to the Internet. The IP address of the internal interface on Router2 is 10.1.14.254.
You need to configure Server1 to use Router2 to connect to the Internet if Router1 fails.
What should you do on Server1?
A. Add a route for 10.1.14.0/24 that uses 10.1.14.254 as the gateway and set the metric to 500.
B. Add 10.1.14.254 as a gateway and set the metric to 500.
C. Add a route for 10.1.14.0/24 that uses 10.1.14.254 as the gateway and set the metric to 1.
D. Add 10.1.14.254 as a gateway and set the metric to 1.
Answer: B
Explanation:
To configure the Automatic Metric feature:
1. In Control Panel, double-click Network Connections.
2. Right-click a network interface, and then click Properties.
3. Click Internet Protocol (TCP/IP), and then click Properties.
4. On the General tab, click Advanced.
5. To specify a metric, on the IP Settings tab, click to clear the Automatic metric check box, and then enter the metric that you want in the Interface Metric field.
To manually add routes for IPv4
Open the Command Prompt window by clicking the Start button Picture of the Start button.
In the search box, type Command Prompt, and then, in the list of results, click Command Prompt.
At the command prompt, type route -p add [destination] [mask <netmask>] [gateway]
[metric <metric>] [if <interface>].
QUESTION 219
Your network contains and Active Directory domain named contoso.com. The domain contains a member server named Server1. All servers run Server 2012.
You need to collect the error events from all the servers on Server1. The solution ensure that when new servers are added to the domain, their error events are collected automatically on Server1.
Which two actions should you perform?
(Each correct answer presents part of the solution. Choose two.)
A. On Server1, create a source computer initiated subscription.
B. From a Group Policy object (GPO), configure the Configure forwarder resource usage settings.
C. From a Group Policy object (GPO), configure the Configure target Subscription Manager settings
D. On Server1, create a collector initiated subscription.
Answer: AC
Explanation:
A. Source-initiated subscriptions allow you to define a subscription on an event collector computer without defining the event source computers, and then multiple remote event source computers can be set up (using a group policy setting) to forward events to the event collector computer.
C. Enable the SubscriptionManager setting, and click the Show button to add a server address to the setting.
http://technet.microsoft.com/en-us/library/cc722010.aspx
http://msdn.microsoft.com/en-us/library/windows/desktop/bb870973(v=vs.85).aspx
QUESTION 220
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. DirectAccess is deployed to the network. Remote users connect to the DirectAccess server by using a variety of network speeds. The remote users report that sometimes their connection is very slow.
You need to minimize Group Policy processing across all wireless wide area network (WWAN) connections.
Which Group Policy setting should you configure?
A. Configure Group Policy slow link detection.
B. Configure wireless policy processing.
C. Change Group Policy processing to run asynchronously when a slow network connection is detected.
D. Configure Direct Access connections as a fast network connection.
Answer: A
Explanation:
http://www.rebeladmin.com/tag/slow-link/
GreatExam is the leader in supplying candidates with current and up-to-date training materials for Microsoft certification and exam preparation. Comparing with others, our 70-411 exam questions are more authoritative and complete. We offer the latest 70-411 PDF and VCE dumps with new version VCE player for free download, and the new 70-411 practice test ensures your exam 100% pass.