Are you worring about the 70-342 exam? With the complete collection of 70-342 exam questions and answers, GreatExam has assembled to take you through your 70-342 exam preparation. Each Q & A set will test your existing knowledge of 70-342 fundamentals, and offer you the latest training products that guarantee you passing 70-342 exam easily.
QUESTION 161
You have an Exchange Server 2013 organization that has a hybrid deployment with Microsoft Office 365. The hybrid deployment use Active Directory Federation Services (AD FS) 3.0.
You need to ensure that only Exchange ActiveSync devices are allowed to access Office 365 services from outside of the organization.
Which two actions should you perform? Each correct answer presents part of the solution.
A. Create a Mobile Device Mailbox Policy.
B. Update the Office 365 Identify Platform relying party trust.
C. Add claims rules to the Active Directory claims provider trust.
D. Update the Office mobile device policy.
E. Add an Active Directory Identify Platform relying party trust.
Answer: BC
Explanation:
Step 1: Add claim rules to the Active Directory Claims Provider trust Block all external access to Office 365 except Exchange ActiveSync
The following example allows access to all Office 365 applications, including Exchange Online, from internal clients including Outlook. It blocks access from clients residing outside the corporate network, as indicated by the client IP address, except for Exchange ActiveSync clients such as smart phones. The rule set builds on the default Issuance Authorization rule titled Permit Access to All Users. Use the following steps to add an Issuance Authorization rule to the Office 365 relying party trust using the Claim Rule Wizard: (steps omitted).
Step 2: Update the Microsoft Office 365 Identity Platform relying party trust
https://technet.microsoft.com/en-us/library/hh526961(v=ws.10).aspx
QUESTION 162
You have an Exchange Server 2013 organization that is integrated with Microsoft Lync Server 2013. Users report that they fail to make Unified Messaging (UM) calls.
You need to perform an end-to-end test of the UM components.
Which cmdlet should you use?
A. Test-ExchangeUMCallFlow
B. Test-CsPhoneBootstrap
C. Start-UMPhoneSession
D. Test-UMConnectivity
Answer: A
Explanation:
Use the Test-ExchangeUMCallFlow cmdlet (the UM Troubleshooting Tool) to test call flow between Client Access servers running the Microsoft Exchange Unified Messaging Call Router service, Mailbox servers running the Microsoft Exchange Unified Messaging service, VoIP gateways, IP PBXs, Session Initiation Protocol (SIP) servers and Microsoft Lync Server.
The Test-ExchangeUMCallFlow cmdlet can be used to diagnose configuration errors found in telephony components, Exchange 2010 SP1 or later or Exchange 2013 Unified Messaging settings, and connectivity issues between on-premises and hybrid Unified Messaging deployments.
https://technet.microsoft.com/en-us/library/ff630913%28v=exchg.150%29.aspx
QUESTION 163
Your company has two offices. The offices are located in New York and Tokyo.
You have an Exchange Server 2013 organization.
You have the following Unified Messaging (UM) dial plans:
– Tokyo Dial Plan
– New York Dial Plan
A user named User 1 has a mailbox that is associated with the New York Dial Plan. User 1 frequently works from both the New York and the Tokyo offices.
You need to add an extension from the Tokyo office to the account of User1.
Which cmdlet should you run?
A. Set-Mailbox
B. Set-UMMailbox
C. Set-UMMailboxPolicy
D. Set-UMDialPlan
Answer: D
Explanation:
Use the Set-UMDialplan cmdlet to set various properties on a Unified Messaging (UM) dial plan.
The Extension parameter specifies the extension number used by the Call Someone feature when a call is transferred.
https://technet.microsoft.com/en-us/library/bb124408(v=exchg.150).aspx
QUESTION 164
Hotspot Question
You have an Exchange Server 2013 organization.
You need to create a single transport rule that applies to messages sent from users in the organization to users that are outside of the organization.
Which two options should you use? To answer, select the two appropriate options in the answer area.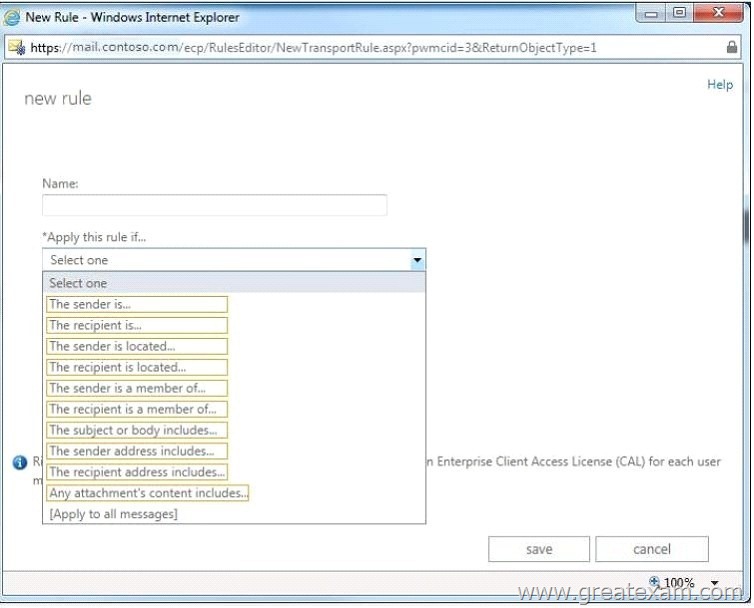
Answer: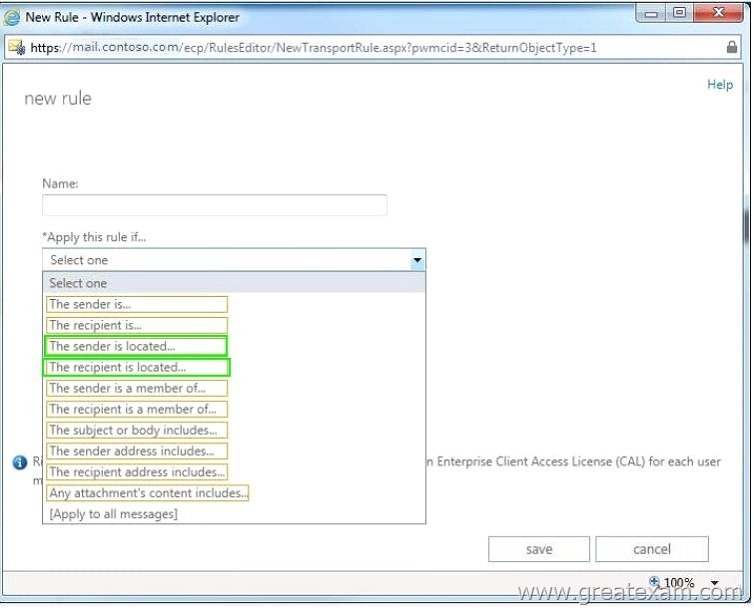
QUESTION 165
Hotspot Question
You have an Exchange Server 2013 organization named contoso.com.
Contoso.com has a federated trust to another Exchange Server 2013 organization named fabrikam.com.
You need to ensure that users from fabrikam.com can view the availability of users in contoso.com.
What command should you run? To answer, select the appropriate options in the answer area.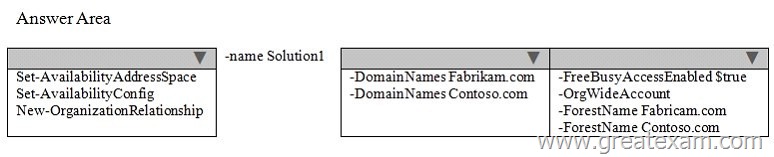
Answer: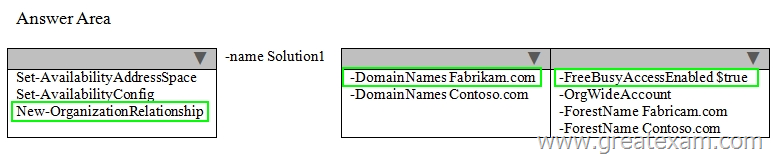
QUESTION 166
Hotspot Question
You have an Exchange Server 2013 organization and a Microsoft SharePoint Server 2013 server farm.
You plan to use a SharePoint eDiscovery Center.
You need to recommend which component must be deployed before you can use the SharePoint eDiscovery Center for In-Place eDiscovery.
What should you recommend? To answer, select the appropriate options in the answer area.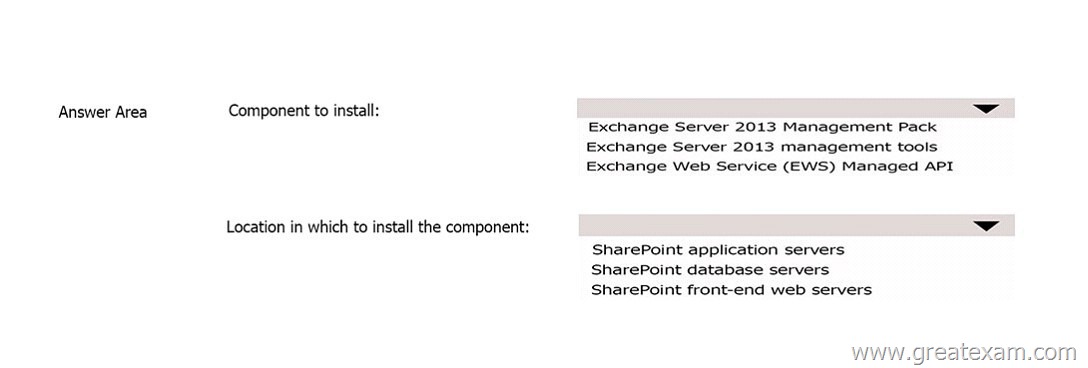
Answer: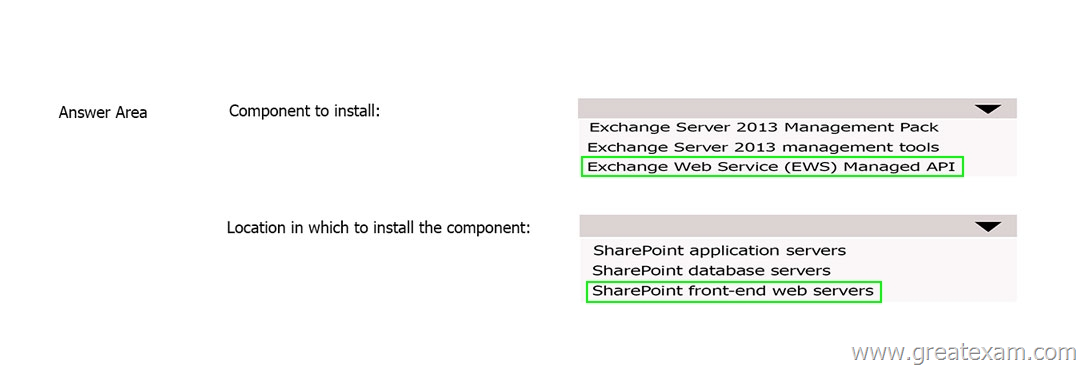
QUESTION 167
You have an Exchange Server 2013 organization that is integrated with Information Rights Management (IRM).
A user is unable to create and read IRM-protected messages from a mobile device.
The user can open IRM- protected messages *missing text*.
You need to identify the most likely cause of the issue.
What should you identify?
A. the value of DevicePasswordEnabled of a mobile device policy
B. the value of AllowNonProvisionableDevices of a mobile device policy
C. the Exchange ActiveSync protocol version
D. the value of RequireDeviceEncryption of a mobile device policy
Answer: D
Explanation:
Mobile IRM protection in Exchange 2013 When you set the RequireDeviceEncryption parameter to $true, mobile devices that don’t support device encryption will be unable to connect.
Note: Using IRM in Exchange ActiveSync, mobile device users can:
* Create IRM-protected messages.
* Read IRM-protected messages.
* Reply to and forward IRM-protected messages.
https://technet.microsoft.com/en-us/library/ff657743(v=exchg.150).aspx
QUESTION 168
You have a server named Server1 that has Exchange Server 2013 installed.
Users access their mailbox by using Microsoft Outlook 2010 and Outlook Web App.
You need to identify when a mailbox is accessed by someone other than the owner of the mailbox.
Which two actions should you perform? Each correct answer presents part of the solution.
A. Review the security event log.
B. Enable audit logging for all mailboxes.
C. Export the administrator audit log.
D. Run an administrator role group report.
E. Run a non-owner mailbox access report.
Answer: BE
Explanation:
You have to enable mailbox audit logging for each mailbox that you want to run a non-owner mailbox access report.
The Non-Owner Mailbox Access Report in the Exchange Administration Center (EAC) lists the mailboxes that have been accessed by someone other than the person who owns the mailbox. When a mailbox is accessed by a non-owner, Microsoft Exchange logs information about this action in a mailbox audit log that’s stored as an email message in a hidden folder in the mailbox being audited. Entries from this log are displayed as search results and include a list of mailboxes accessed by a non-owner, who accessed the mailbox and when, the actions performed by the non-owner, and whether the action was successful.
https://technet.microsoft.com/en-us/library/jj150575(v=exchg.150).aspx
QUESTION 169
Hotspot Question
You have an Exchange Server 2013 organization that contains the servers configured as shown in the following table.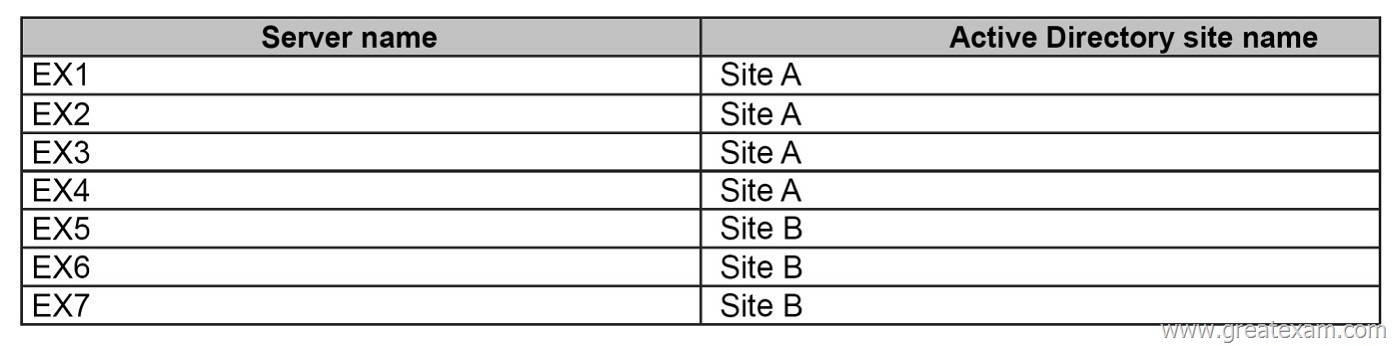
All of the Exchange servers run Windows Server 2012 R2 and are members of a database availability group (DAG) named DAG1.
A mailbox database named DB1 replicates between EX1, EX2, EX3, and EX7. The mailbox database copy of DB1 on EX7 is a lagged database.
You need to ensure that if the number of healthy database copies of DB1 is less than three during a 24-hour period, the logs in the lagged database replay automatically.
What command should you run? To answer, select the appropriate options in the answer area.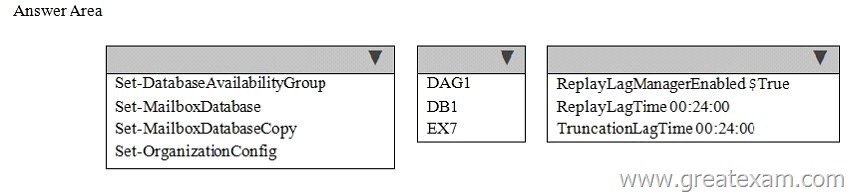
Answer: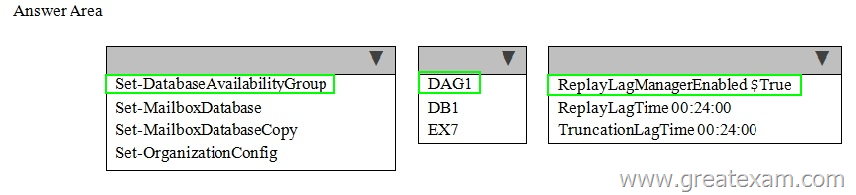
QUESTION 170
You have an Exchange Server 2013 organization that contains the servers configured as shown in the following table.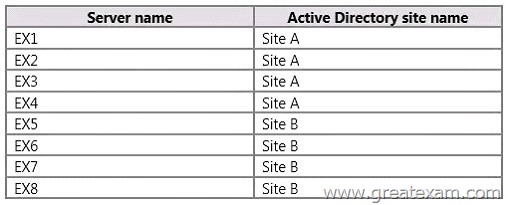
All of the Exchange servers run Windows Server 2012 R2 and are members of a database
availability group (DAG) named DAG1. Each server has a copy of all the mailbox databases.
DAG1 is configured to have a cluster administrative access point. The file share witness is located in Site A.
EX5 fails and is taken offline permanently.
You need to identify the maximum number of Mailbox servers that can fail simultaneously without affecting the mailbox access of the users.
How many servers should you identify?
A. 2
B. 3
C. 4
D. 5
Answer: B
QUESTION 171
You have an Exchange Server 2013 organization.
You plan to use document fingerprinting.
You need to identify which file type cannot be used as a template for document fingerprinting.
Which document type should you identify?
A. .pptx
B. .doc
C. .txt
D. .dotx
Answer: D
Explanation:
Document Fingerprinting supports the same file types that are supported in transport rules. One quick note about file types: neither transport rules nor Document Fingerprinting supports the .dotx file type, which can be confusing because that’s a template file in Word. When you see the word “template” in this and other Document Fingerprinting topics, it refers to a document that you have established as a standard form, not the template file type.
https://technet.microsoft.com/en-us/library/dn635176(v=exchg.150).aspx
QUESTION 172
Hotspot Question
You have an Exchange Server 2013 organization that contains two servers named EX1 and EX2. Both servers are in the same Active Directory site.
You run Get-TransportConfig | fi “shadow” and you receive the following output.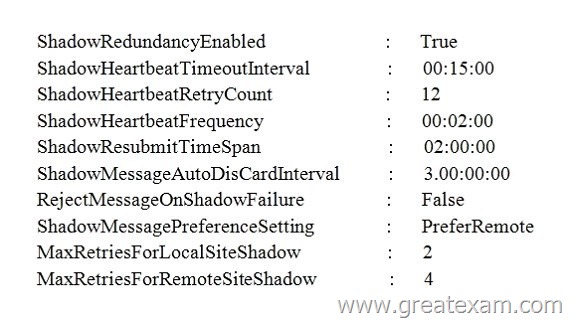
Use the drop-down menus to select the answer choice that completes each statement.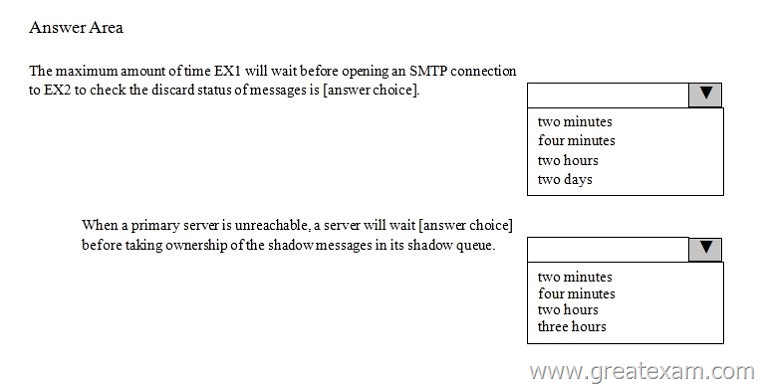
Answer:
QUESTION 173
Hotspot Question
You have an Exchange Server 2013 organization.
You plan to implement a hybrid deployment with Microsoft Office 365. Active Directory Federation services (AD FS) will be used to provide Single Sign-On (SSO). Users will access the hybrid deployment by using Microsoft Outlook 2013 and mobile devices.
A user named User1 changes the password for his on-promises Active Directory user account.
You need to identify whether User1 will be prompted for a password when accessing his mailbox from various client types.
In the table below identify whether User1 will be prompted for a password when accessing his mailbox from various clients.
NOTE: Make only one selection in each row.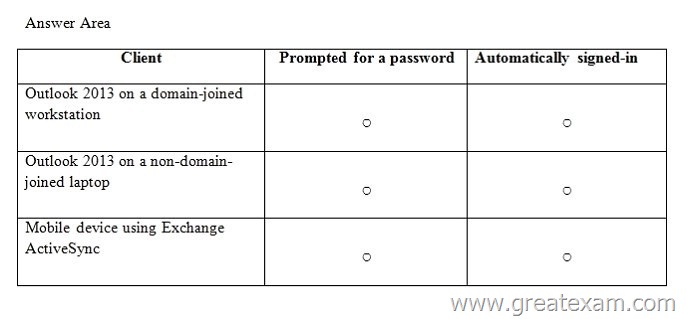
Answer: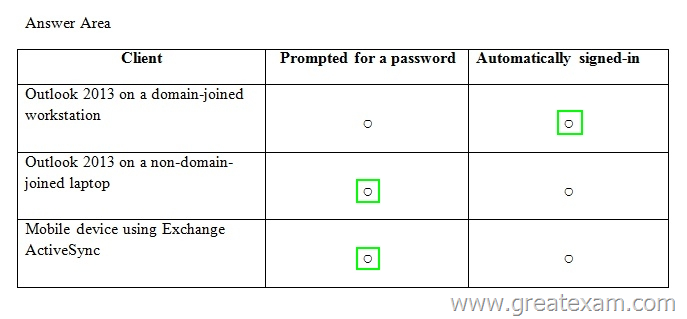
QUESTION 174
Drag and Drop Question
Your company has two offices. Each office is configured as an Active Directory site.
The sites are named Site1 and Site2.
You have an Exchange Server 2013 organization that is configured as shown in the following exhibit. (Click the Exhibit button.)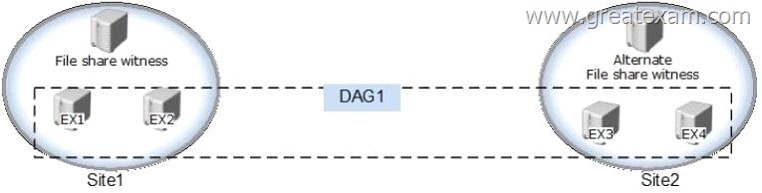
Datacenter Activation Coordination (DAC) mode is enabled on the database availability group (DAG) named DAG1.
You are testing a site failover by shutting down all of the servers in Site1.
You need to mount the databases in Site2.
Which four commands should you run in sequence? (To answer, move the appropriate four commands from the list of commands to the answer area and arrange them in the correct order. More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.)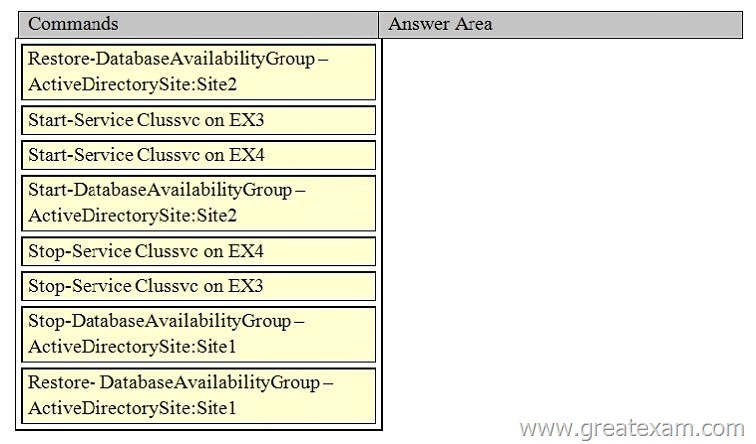
Answer: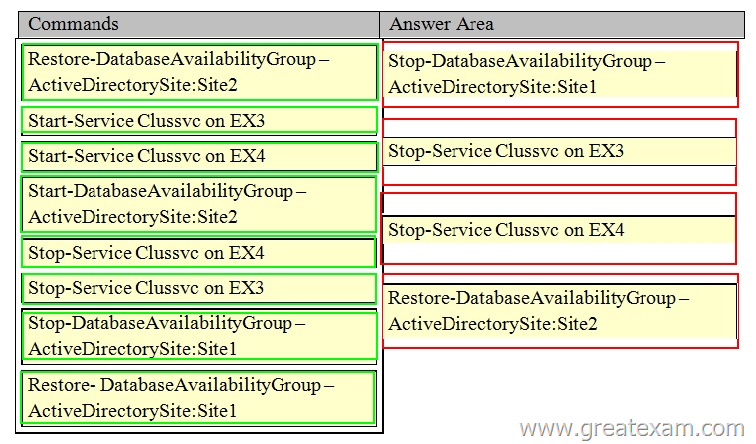
QUESTION 175
You have an Exchange Server organization that contains Exchange Server 2010 servers and Exchange Server 2013 servers.
You have a Microsoft Lync Server 2010 environment that is integrated with Unified Messaging (UM) services.
You have an Exchange Server 2010 server named EX1 that has the Unified Messaging server role installed.
You are migrating the UM services to Exchange Server 2013.
You need to prevent EX1 from providing call answering services during the migration.
What should you modify?
A. the UM mailbox policies
B. the UM auto attendants
C. the UM dial plans
D. the UM hunt groups
Answer: C
Explanation:
https://technet.microsoft.com/en-us/library/dn169226%28v=exchg.150%29.aspx
At GreatExam, we are positive that our Microsoft 70-342 preparation material with questions and answers PDF provide most in-depth solutions for individuals that are preparing for the Microsoft 70-342 exam. Our updated 70-342 braindumps will allow you the opportunity to know exactly what to expect on the exam day and ensure that you can pass the exam beyond any doubt.