Our PDF dumps of 70-414 exam is designed to ensure everything which you need to pass your exam successfully. At GreatExam, we have a completely customer oriented policy. We invite the professionals who have rich experience and expert knowledge of the IT certification industry to guarantee the PDF details precisely and logically. Our customers’ time is a precious concern for us. This requires us to provide you the products that can be utilized most efficiently.
QUESTION 101
You need to implement a solution for the email attachments.
Both organizations exchange root CA certificates and install the certificates in the relevant stores.
You duplicate the Enrollment Agent certificate template and generate a certificate based on the new template.
Which additional two actions should you perform? Each Answer presents part of the solution.
A. Request cross-certification authority certificates.
B. Create Capolicy.inf files.
C. Request subordinate CA certificates.
D. Create Policy.inf files.
Answer: AD
Explanation:
See “Creating Trust Between Two Organizations”
https://technet.microsoft.com/en-us/library/cc785267(v=ws.10).aspx
Creating Trust Between Two Organizations
The second scenario where cross-certification may be used is to allow certificates to be used and trusted between two organizations. Before the cross-certification is performed between the two organizations, the first thing that must be decided is what certificate usage will be trusted between the organizations. For example, you could require that certificates be trusted from the other organization(s) only for secure e-mail. Or, you could allow secure e-mail, client authentication, and server authentication.
This must be decided and included in the Policy.inf file when the qualified subordination is configured between CAs in the two organizations.
QUESTION 102
You need to recommend a design that meets the technical requirements for managing the Hyper-V hosts by using VMM.
What should you recommend? To answer, select the appropriate options in the answer area.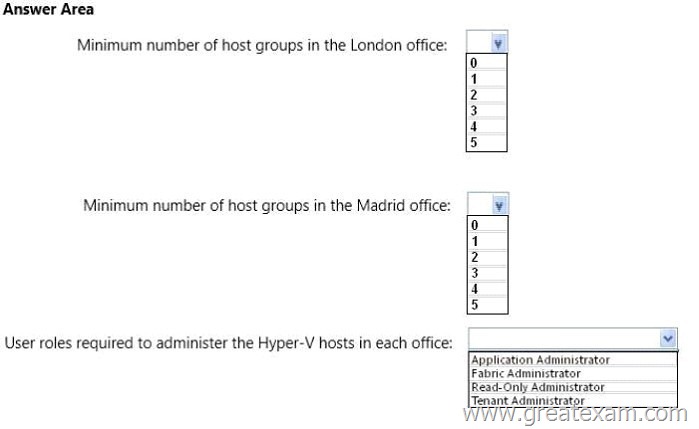
Answer: 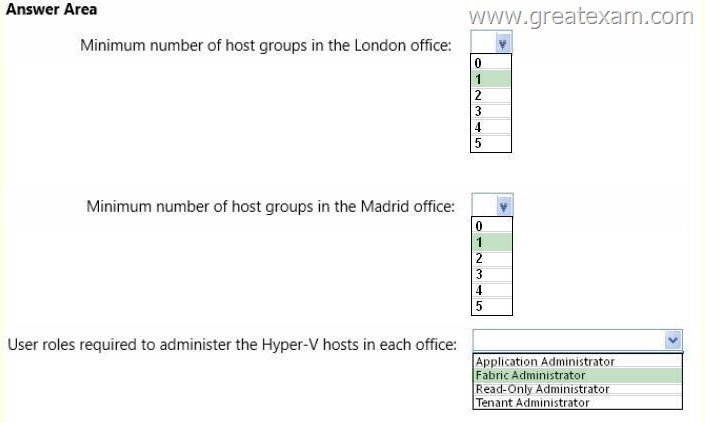
QUESTION 103
You need to recommend a monitoring solution for Proseware.
Which three actions should you recommend performing in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.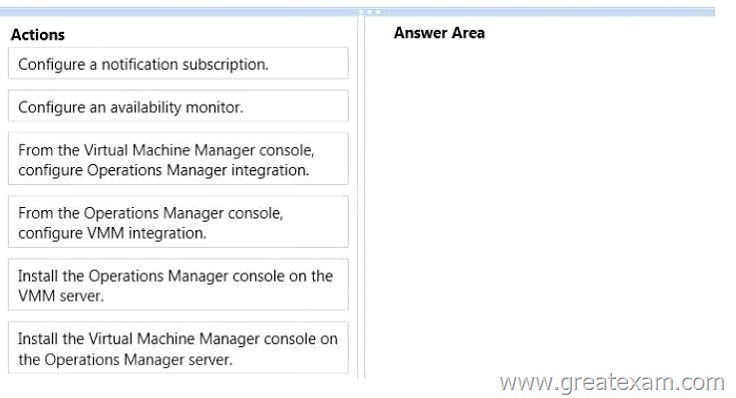
Answer: 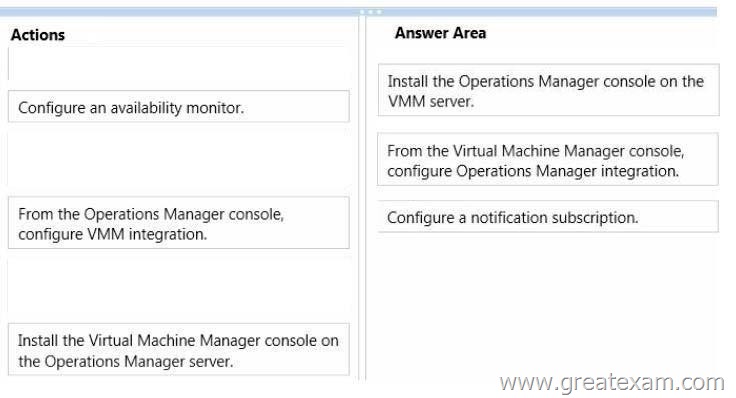
Case Study 4: Northwind Traders (QUESTION 104 – QUESTION 114)
Overview
Northwind Traders is an IT services and hosting provider.
Northwind Traders has two main data centers in North America.
The data centers are located in the same city.
The data centers connect to each other by using high-bandwidth, low-latency WAN links.
Each data center connects directly to the Internet.
Northwind Traders also has a remote office in Asia that connects to both of the North American data centers by using a WAN link.
The Asian office has 30 multipurpose servers.
Each North American data center contains two separate network segments.
One network segment is used to host the internal servers of Northwind Traders.
The other network segment is used for the hosted customer environments.
Existing Environment
Active Directory
The network contains an Active Directory forest named northwindtraders.com.
The forest contains a single domain.
All servers run Windows Server 2012 R2.
Server Environment
The network has the following technologies deployed:
– Service Provider Foundation
– Windows Azure Pack for Windows Server
– System Center 2012 R2 Virtual Machine Manager (VMM)
– An Active Directory Rights Management Services (AD RMS) cluster
– An Active Directory Certificate Services (AD CS) enterprise certification authority (CA)
All newly deployed servers will include the following components:
– Dual 10-GbE Remote Direct Memory Access (RDMA)-capable network adapters
– Dual 1-GbE network adapters
– 128 GB of RAM
Requirements
Business Goals
Northwind Traders will provide hosting services to two customers named Customer1 and Customer2.
The network of each customer is configured as shown in the following table.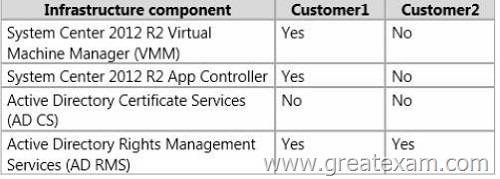
Planned Changes
Northwind Traders plans to implement the following changes:
– Deploy System Center 2012 R2 Operations Manager.
– Deploy Windows Server 2012 R2 iSCSI and SMB-based storage.
– Implement Hyper-V Recovery Manager to protect virtual machines.
– Deploy a certificate revocation list (CRL) distribution point (CDP) on the internal network.
– For Customer 1, install server authentication certificates issued by the CA of Northwind Traders on the virtual machine in the hosting networks.
General Requirements
Northwind Traders identifies the following requirements:
– Storage traffic must use dedicated adapters.
– All storage and network traffic must be load balanced.
– The amount of network traffic between the internal network and the hosting network must be minimized.
– The publication of CRLs to CDPs must be automatic.
– Each customer must use dedicated Hyper-V hosts.
– Administrative effort must be minimized, whenever possible.
– All servers and networks must be monitored by using Operations Manager.
– Anonymous access to internal file shares from the hosting network must be prohibited.
– All Hyper-V hosts must use Cluster Shared Volume (CSV) shared storage to host virtual machines.
– All Hyper-V storage and network traffic must remain available if single network adapter fails.
– The Hyper-V hosts connected to the SMB-based storage must be able to make use of the RDMA technology.
– The number of servers and ports in the hosting environment to which the customer has access must be minimized.
Customer1 Requirements
Northwind Traders identifies the following requirements for Customer1:
– Customer1 must use SMB-based storage exclusively.
– Customer1 must use App Controller to manage hosted virtual machines.
– The virtual machines of Customer1 must be recoverable if a single data center fails.
– Customer1 must be able to delegate self-service roles in its hosted environment to its users.
– Customer1 must be able to check for the revocation of certificates issued by the CA of Northwind Traders.
– The users of Customer1 must be able to obtain use licenses for documents protected by the AD RMS of Northwind Traders.
– Certificates issued to the virtual machines of Customer1 that reside on the hosted networks must be renewed automatically.
Customer2 Requirements
Northwind Traders identifies the following requirements for Customer2:
– Customer2 must use iSCSI-based storage exclusively.
– All of the virtual machines of Customer2 must be migrated by using a SAN transfer.
– None of the metadata from the virtual machines of Customer2 must be stored in Windows Azure.
– The network configuration of the Hyper-V hosts for Customer2 must be controlled by using logical switches.
– The only VMM network port profiles and classifications allowed by Customer2 must be low-bandwidth, medium-bandwidth, or high-bandwidth.
– The users at Northwind Traders must be able to obtain use licenses for documents protected by the AD RMS cluster of Customer2. Customer2 plans to decommission its AD RMS cluster during the next year.
QUESTION 104
You need to recommend a monitoring solution for Northwind Traders.
What is the best approach to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
A. Three Operations Manager management servers and two Operations Manager gateway servers
B. One Operations Manager management server
C. Two Operations Manager management servers and three Operations Manager gateway servers
D. Five Operations Manager management servers
Answer: C
QUESTION 105
You plan to implement a solution that meets the certificate requirements of Customer1.
You need to identify which role services must be deployed to the hosting environment.
Which two role services should you identify? Each Answer presents part of the solution.
A. Certification Authority Web Enrollment
B. Online Responder
C. Certificate Enrollment Policy Web Service
D. Certificate Enrollment Web Service
Answer: CD
QUESTION 106
You need to recommend changes to allow Customer1 to delegate permissions in its hosting environment to its users.
Where should you recommend performing each task? To answer, select the appropriate location for each task in the answer area.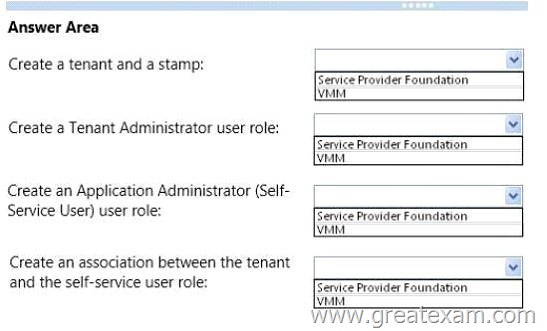
Answer: 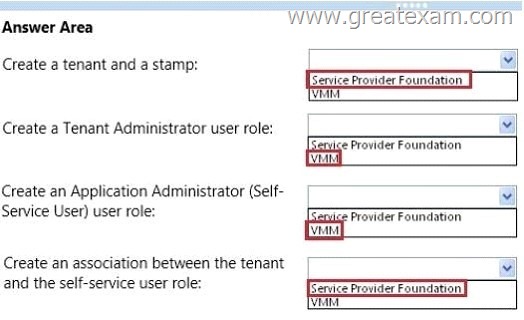
QUESTION 107
You need to recommend a solution that meets the AD RMS requirements of Customer1 and Customer2.
Which actions should you recommend performing for each customer? To answer, select the appropriate customer for each action in the answer area.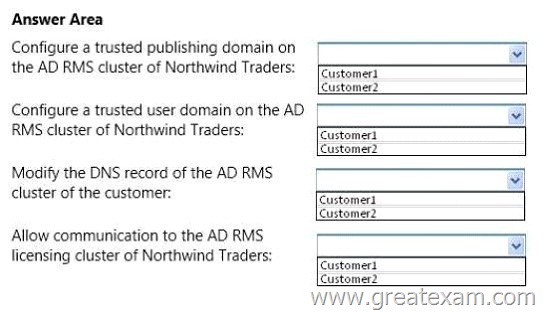
Answer: 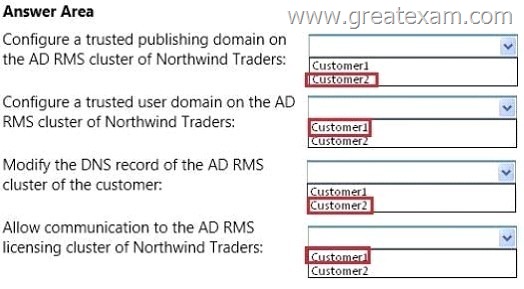
QUESTION 108
You need to prepare for the migration of virtual machines across the Hyper-V hosts of Customer2.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.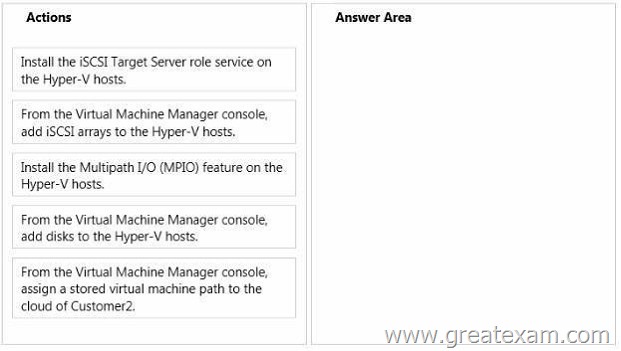
Answer: 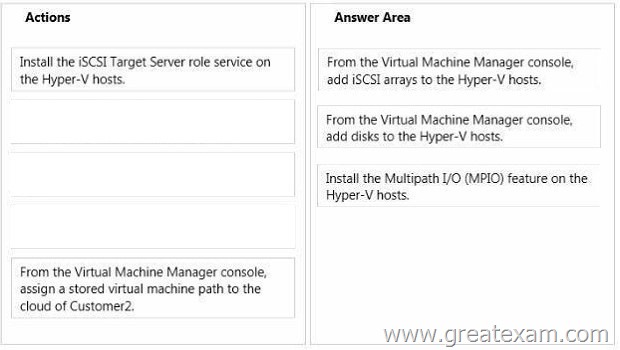
Explanation:
http://blogs.technet.com/b/keithmayer/archive/2013/03/12/speaking-iscsi-with-windows-server-2012-and-hyper-v.aspx
QUESTION 109
You need to recommend a network configuration for the newly deployed Hyper-V hosts used by Customer1.
On which network adapter should you recommend performing each configuration? To answer, select the appropriate network adapter for each configuration in the answer area.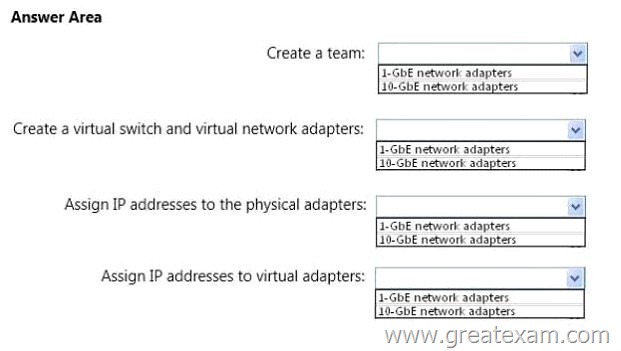
Answer: 
QUESTION 110
You need to recommend which setting must be applied to the virtualization infrastructure of Northwind Traders to minimize the impact of multiple virtual machines starting concurrently.
What command should you recommend running? To answer, select the appropriate options in the answer area.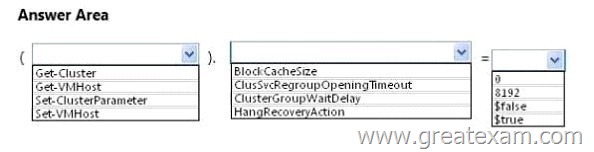
Answer: 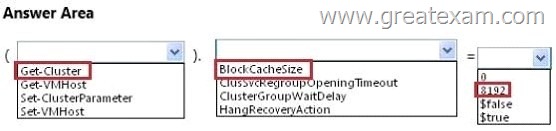
QUESTION 111
You need to prepare the required Hyper-V virtual network components for Customer2.
Which four objects should you create and configure in sequence? To answer, move the appropriate objects from the list of objects to the answer area and arrange them in the correct order.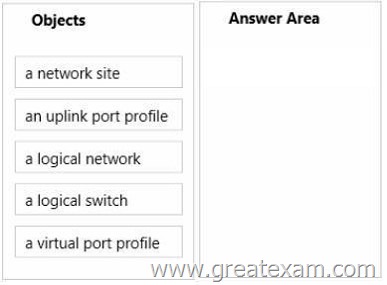
Answer: 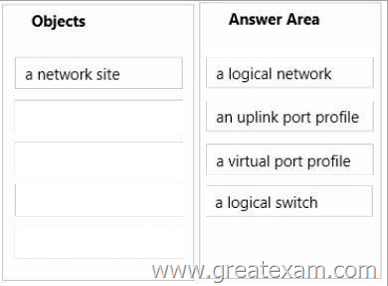
Explanation:
The recommended sequence for creating port profiles and logical switches is to create the port profiles first. You will need at least one port profile for uplinks before you can create a logical switch.
https://technet.microsoft.com/en-us/library/jj628166.aspx
QUESTION 112
You need to implement a Hyper-V Recovery Manager solution in the hosting environment of Northwind Traders.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.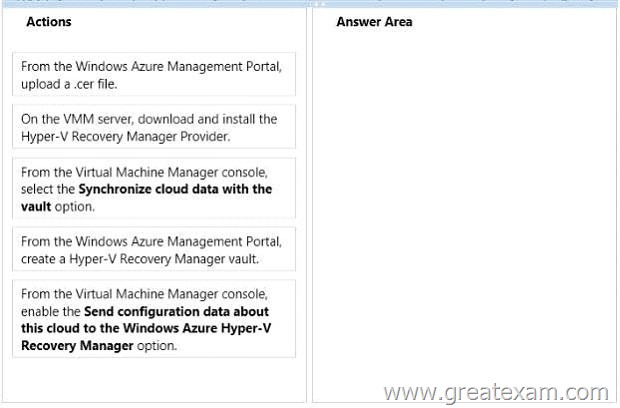
Answer: 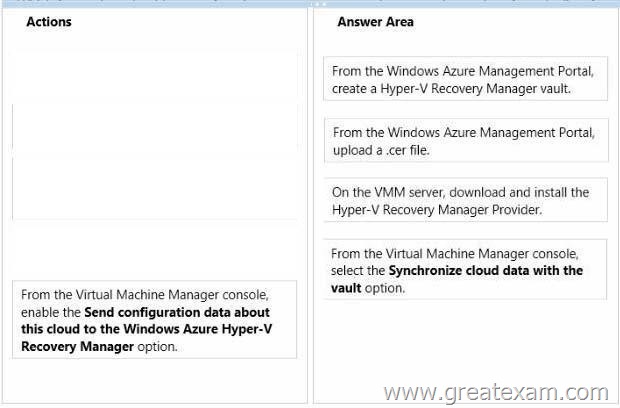
Explanation:
http://azure.microsoft.com/en-us/documentation/articles/hyper-v-recovery-manager-azure/
QUESTION 113
You need to recommend a configuration for the CA extensions of Northwind Traders that meets the certificate revocation requirement of Customer1.
What should you recommend? To answer, select the appropriate prefix of the target location for the each extension settings in the answer area.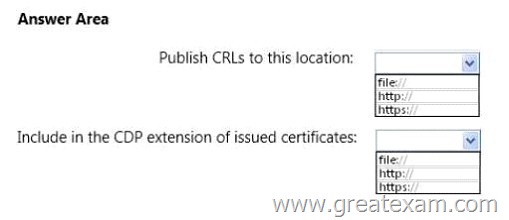
Answer: 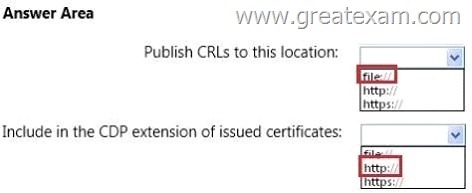
QUESTION 114
Your network contains a main data center and a disaster recovery data center.
Each data center contains a Storage Area Network (SAN).
The main data center contains a two-node failover cluster named Cluster1 that hosts a Microsoft SQL Server 2012 database named DB1.
The database files in DB1 are stored on the SAN in the main office.
The disaster recovery data center contains a server that runs SQL Server 2012.
You need to recommend a disaster recovery solution for the SQL Server database.
The solution must ensure that the database remains available if the main data center fails.
What should you recommend? More than one answer choice may achieve the goal. Select the BEST answer.
A. Deploy Distributed File System (DFS) Replication.
B. Extend the failover cluster to the disaster recovery data center.
C. Implement a Cluster Shared Volume (CSV) and move the database files to the CSV.
D. Implement SQL Server database replication between the two data centers.
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/ms151198.aspx
QUESTION 115
Your Active Directory currently contains five virtualized domain controllers that run Windows Server 2012 R2.
The system state of each domain controller is backed up daily.
The backups are shipped to a remote location weekly.
Your company recently implemented a disaster recovery site that contains several servers.
The servers run Windows Server 2012 R2 and have the Hyper-V server role installed.
The disaster recovery site has a high-speed WAN link to the main office.
You need to create an Active Directory recovery plan that meets the following requirements:
– Restores the Active Directory if a catastrophe prevents all access to the main office.
– Minimizes data loss.
What should you include in the plan?
A. Hyper-V replicas
B. Live migration
C. Virtual machine checkpoints
D. System state restores
Answer: A
QUESTION 116
Your network contains 500 client computers that run Windows 7 and a custom application named App1.
App1 uses data stored in a shared folder.
You have a failover cluster named Cluster1 that contains two servers named Server1 and Server2. Server1 and Server2 run Windows Server 2012 and are connected to an iSCSI Storage Area Network (SAN).
You plan to move the shared folder to Cluster1.
You need to recommend which cluster resource must be created to ensure that the shared folder can be accessed from Cluster1.
What should you recommend? More than one answer choice may achieve the goal. Select the BEST answer.
A. The Generic Application cluster role
B. The DFS Namespace Server cluster role
C. The clustered File Server role of the File Server for general use type
D. The clustered File Server role of the File Server for scale-out application data type
Answer: C
QUESTION 117
Your network contains five servers that run Windows Server 2012 R2.
You install the Hyper-V server role on the servers.
You create an external virtual network switch on each server.
You plan to deploy five virtual machines to each Hyper-V server.
Each virtual machine will have a virtual network adapter that is connected to the external virtual network switch and that has a VLAN identifier of 1.
Each virtual machine will run Windows Server 2012 R2.
All of the virtual machines will run the identical web application.
You plan to install the Network Load Balancing (NLB) feature on each virtual machine and join each virtual machine to an NLB cluster.
The cluster will be configured to use unicast only.
You need to ensure that the NLB feature can distribute connections across all of the virtual machines.
Solution: From the properties of each virtual machine, you enable MAC address spoofing for the existing virtual network adapter.
Does this meet the goal?
A. Yes
B. No
Answer: A
QUESTION 118
Your network contains five servers that run Windows Server 2012 R2.
You install the Hyper-V server role on the servers.
You create an external virtual network switch on each server.
You plan to deploy five virtual machines to each Hyper-V server.
Each virtual machine will have a virtual network adapter that is connected to the external virtual network switch and that has a VLAN identifier of 1.
Each virtual machine will run Windows Server 2012 R2.
All of the virtual machines will run the identical web application.
You plan to install the Network Load Balancing (NLB) feature on each virtual machine and join each virtual machine to an NLB cluster.
The cluster will be configured to use unicast only.
You need to ensure that the NLB feature can distribute connections across all of the virtual machines.
Solution: On each Hyper-V server, you create a new external virtual network switch.
From the properties of each virtual machine, you add a second virtual network adapter and connect the new virtual network adapters to the new external virtual network switches.
Does this meet the goal?
A. Yes
B. No
Answer: B
QUESTION 119
Your network contains five servers that run Windows Server 2012 R2.
You install the Hyper-V server role on the servers.
You create an external virtual network switch on each server.
You plan to deploy five virtual machines to each Hyper-V server.
Each virtual machine will have a virtual network adapter that is connected to the external virtual network switch and that has a VLAN identifier of 1.
Each virtual machine will run Windows Server 2012 R2. All of the virtual machines will run the identical web application.
You plan to install the Network Load Balancing (NLB) feature on each virtual machine and join each virtual machine to an NLB cluster.
The cluster will be configured to use unicast only.
You need to ensure that the NLB feature can distribute connections across all of the virtual machines.
Solution: On each Hyper-V server, you create a new private virtual network switch.
From the properties of each virtual machine, you add a second virtual network adapter and connect the new virtual network adapters to the new private virtual network switches.
Does this meet the goal?
A. Yes
B. No
Answer: B
QUESTION 120
Your network contains five servers that run Windows Server 2012 R2.
You install the Hyper-V server role on the servers.
You create an external virtual network switch on each server.
You plan to deploy five virtual machines to each Hyper-V server.
Each virtual machine will have a virtual network adapter that is connected to the external virtual network switch and that has a VLAN identifier of 1.
Each virtual machine will run Windows Server 2012 R2. All of the virtual machines will run the identical web application.
You plan to install the Network Load Balancing (NLB) feature on each virtual machine and join each virtual machine to an NLB cluster.
The cluster will be configured to use unicast only.
You need to ensure that the NLB feature can distribute connections across all of the virtual machines.
Solution: From the properties of each virtual machine, you add a second virtual network adapter. You connect the new virtual network adapters to the external virtual network switch and configure the new virtual network adapters to use a VLAN identifier of 2.
Does this meet the goal?
A. Yes
B. No
Answer: B
If you want to get more 70-414 exam preparation material, you can download the free 70-414 braindumps in PDF files on GreatExam. It would be great helpful for your exam. All the 70-414 dumps are updated and cover every aspect of the examination. Welcome to choose.