GreatExam 70-412 study guide provides you everything you will need to take your 70-412 exam. The 70-412 exam details are researched and produced by Professional Certification Experts who are constantly using industry experience to produce precise, and logical. You may get questions from different books, but logic is the key. Our Product will help you not only pass in the first try, but also save your valuable time.
QUESTION 301
Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2.
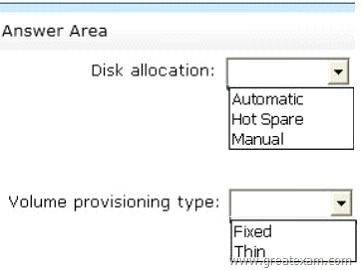
You are configuring a storage space on Server1.
You need to ensure that the storage space supports tiered storage.
Which settings should you configure? To answer, select the appropriate options in the answer area.
QUESTION 302
Hotspot Question
You have a server that runs Windows Server 2012 R2 and has the iSCSI Target Server role service installed.
You run the New-IscsiVirtualDisk cmdlet as shown in the New-IscsiVirtualDisk exhibit.
(Click the Exhibit button.)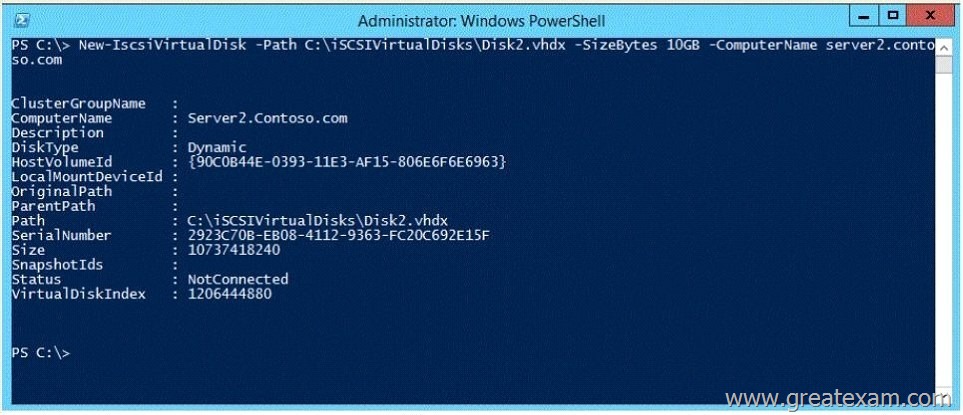
To answer, complete each statement according to the information presented in the exhibits.
Each correct selection is worth one point.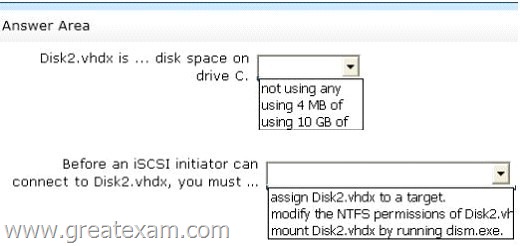
Answer: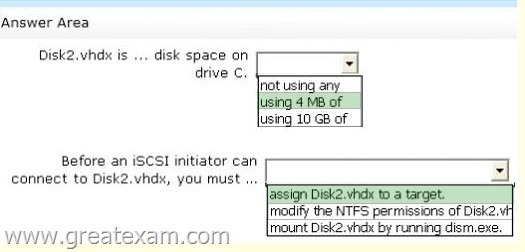
Explanation:
Because you just created the new disk with that powershell command, so it’s BRAND NEW and it’s dynamic, so only 4Mb.
QUESTION 303
Your network contains a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Active Directory Certificate Services server role installed and is configured as a standalone certification authority (CA).
You install a second server named Server2.
You install the Online Responder role service on Server2.
You need to ensure that Server1 can issue an Online Certificate Status Protocol (OCSP) Response Signing certificate to Server2.
What should you run on Server1?
A. The certreq.exe command and specify the -policy parameter
B. The certutil.exe command and specify the -getkey parameter
C. The certutil.exe command and specify the -setreg parameter
D. The certreq.exe command and specify the -retrieve parameter
Answer: C
Explanation:
To prepare a computer running Windows Server to issue OCSP Response Signing certificates
On the server hosting the CA, open a command prompt, and type:
certutil -v -setreg policy\EnableRequestExtensionList +1.3.6.1.5.5.7.48.1.5 Stop and restart the CA. You can do this at a command prompt by running the following commands:
net stop certsvc
net start certsvc
https://technet.microsoft.com/en-us/library/cc732526.aspx
QUESTION 304
Drag and Drop Question
Your network contains two Active Directory forests named contoso.com and adatum.com.
Each forest contains an Active Directory Rights Management Services (AD RMS) root cluster.
All servers run Windows Server 2012 R2.
You need to ensure that the rights account certificates issued in adatum.com are accepted by the AD RMS root cluster in contoso.com.
What should you do in each forest? To answer, drag the appropriate actions to the correct forests. Each action may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Answer: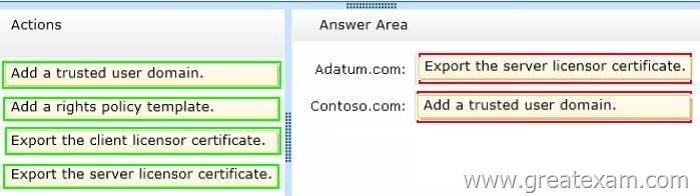
QUESTION 305
Your network contains an Active Directory domain named contoso.com.
All servers run Windows Server 2012 R2.
The domain contains a domain controller named DC1 that is configured as an enterprise root certification authority (CA).
All users in the domain are issued a smart card and are required to log on to their domain- joined client computer by using their smart card.
A user named User1 resigned and started to work for a competing company.
You need to prevent User1 immediately from logging on to any computer in the domain.
The solution must not prevent other users from logging on to the domain.
Which tool should you use?
A. Active Directory Users and Computers
B. Active Directory Sites and Services
C. The Certificates snap-in
D. Server Manager
Answer: A
Explanation:
Disabling or enabling a user account
To open Active Directory Users and Computers, click Start, click Control Panel, double-click
Administrative Tools , and then double-click Active Directory Users and Computers .
To open Active Directory Users and Computers in Windows Server 2012, click Start , type dsa.msc .
In the console tree, click Users .
In the details pane, right-click the user.
Depending on the status of the account, do one of the following:
To disable the account, click Disable Account .
To enable the account, click Enable Account .
QUESTION 306
Your network contains an Active Directory domain named contoso.com.
The domain contains two member servers named Server1 and Server2.
All servers run Windows Server 2012 R2.
Server1 and Server2 have the Failover Clustering feature installed.
The servers are configured as nodes in a failover cluster named Cluster1.
Cluster1 contains a cluster disk resource.
A developer creates an application named App1.
App1 is NOT a cluster-aware application.
App1 runs as a service. App1 stores date on the cluster disk resource.
You need to ensure that App1 runs in Cluster1.
The solution must minimize development effort.
Which cmdlet should you run?
A. Add-ClusterGenericServiceRole
B. Add-ClusterGenericApplicationRole
C. Add-ClusterScaleOutFileServerRole
D. Add-ClusterServerRole
Answer: A
Explanation:
I think it’s A.
The questions says “…App1 runs as a service”
http://technet.microsoft.com/en-us/library/ee460966.aspx
“Configure high availability for a service that was not originally designed to run in a failover cluster.”
If you run an application as a Generic Application, the cluster software will start the application, then periodically query the operating system to see whether the application appears to be running. If so, it is presumed to be online, and will not be restarted or failed over
QUESTION 307
Your network contains an Active Directory domain named contoso.com.
A previous administrator implemented a Proof of Concept installation of Active Directory Rights Management Services (AD RMS).
After the proof of concept was complete, the Active Directory Rights Management Services server role was removed.
You attempt to deploy AD RMS.
During the configuration of AD RMS, you receive an error message indicating that an existing AD RMS Service Connection Point (SCP) was found.
You need to remove the existing AD RMS SCP.
Which tool should you use?
A. Active Directory Users and Computers
B. Authorization Manager
C. Active Directory Domains and Trusts
D. Active Directory Sites and Services
E. Active Directory Rights Management Services
Answer: E
Explanation:
ADRMS will registered the Service Connection Point (SCP) in Active Directory and you will need to unregister first before you remove the ADRMS server role.
If your ADRMS server is still alive, you can easily manually remove the SCP by below:
QUESTION 308
You have a server named SCI that runs a Server Core Installation of Windows Server 2012 R2. Shadow copies are enabled on all volumes.
You need to delete a specific shadow copy.
The solution must minimize server downtime.
Which tool should you use?
A. Shadow
B. Diskshadow
C. Wbadmin
D. Diskpart
Answer: B
Explanation:
DiskShadow.exe is a tool that exposes the functionality offered by the Volume Shadow Copy Service (VSS).
The diskshadow command delete shadows deletes shadow copies.
QUESTION 309
Your network contains an Active Directory domain named contoso.com. The domain contains four servers named Server1, Server2, Server3, and Server4 that run Windows Server 2012 R2.
All servers have the Hyper-V server role and the Failover Clustering feature installed.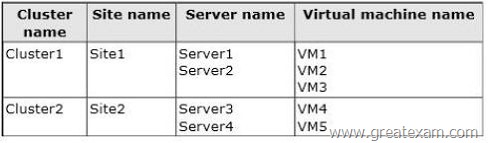
You need to replicate virtual machines from Cluster1 to Cluster2.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. From Hyper-V Manager on a node in Cluster2, create three virtual machines.
B. From Cluster2, add and configure the Hyper-V Replica Broker role.
C. From Failover Cluster Manager on Cluster1, configure each virtual machine for replication.
D. From Cluster1, add and configure the Hyper-V Replica Broker role.
E. From Hyper-V Manager on a node in Cluster2/ modify the Hyper-V settings.
Answer: BCD
Explanation:
These are two clusters, to replicate any VM to a cluster you need to configure the Replica Broker role on each cluster the last step should be enabling replication on the VMs.
https://technet.microsoft.com/en-us/library/jj134240.aspx
“Although Hyper-V Replica will work if you configure only the Replica server (to receive replication from primary servers), it is a GOOD PRACTICE to also configure the primary servers to receive replication. This allows you to reverse the replication direction after a failover, which provides replication protection for the newly active Replica server.”
So as we all know that is clustered environment you configure replica via replica broker so BCD actually make sense as it is the prefered way according to microsoft.
QUESTION 310
You have a server named Server1 that runs Windows Server 2012 R2.
Each day, Server1 is backed up fully to an external disk.
On Server1, the disk that contains the operating system fails.
You replace the failed disk.
You need to perform a bare-metal recovery of Server1 by using the Windows Recovery
Environment (Windows RE).
What should you do?
A. Run the Start-WBVolumeRecovery cmdlet and specify the -backupset parameter.
B. Run the Get-WBBareMetalRecovery cmdlet and specify the -policy parameter.
C. Run the wbadmin.exe start recovery command and specify the –recoverytarget parameter.
D. Run the wbadmin.exe start sysrecovery command and specify the -backuptarget parameter.
Answer: D
Explanation:
wbadmin start sysrecovery
Performs a system recovery (bare metal recovery) using the parameters that you specify.
This subcommand can be run only from the Windows Recovery Environment, and it is not listed by default in the usage text of Wbadmin.
QUESTION 311
You have a server named LON-DC1 that runs Windows Server 2012 R2.
An iSCSI virtual disk named VirtualiSCSI1.vhd exists on LON-DC1 as shown in the exhibit. (Click the Exhibit button.)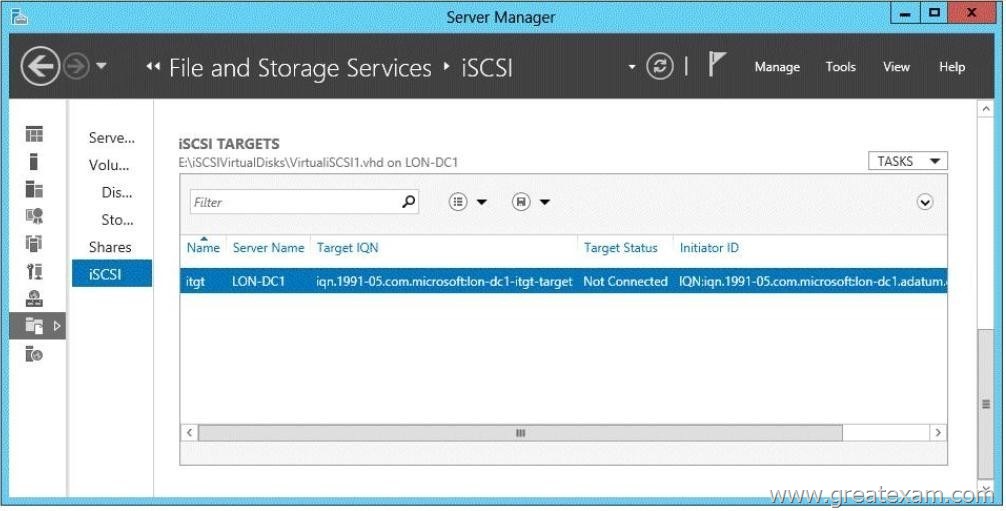
You create a new iSCSI virtual disk named VirtualiSCSI2.vhd by using the existing itgt iSCSI target.
VirtualiSCSIl.vhd is removed from LON-DC1.
You need to assign VirtualiSCSI2.vhd a logical unit value of 0.
What should you do?
A. Modify the properties of the itgt ISCSI target.
B. Modify the properties of the VirtualiSCSI2.vhd iSCSI virtual disk.
C. Run the Set-VirtualDisk cmdlet and specify the -Uniqueld parameter.
D. Run the iscsicli command and specify the reportluns parameter.
Answer: B
Explanation:
The virtual disk has the option to change the lun ID, no other option available in the answers appear to allow this change.
Note: Logical unit numbers (LUNs) created on an iSCSI disk storage subsystem are not directly assigned to a server. For iSCSI, LUNs are assigned to logical entities called targets.
QUESTION 312
Your network contains an Active Directory domain named contoso.com.
All servers run Windows Server 2012 R2.
The domain contains a domain controller named DC1 that is configured as an enterprise root certification authority (CA).
All users in the domain are issued a smart card and are required to log on to their domain- joined client computer by using their smart card.
A user named User1 resigned and started to work for a competing company.
You need to prevent User1 immediately from logging on to any computer in the domain.
The solution must not prevent other users from logging on to the domain.
Which tool should you use?
A. Active Directory Users and Computers
B. Certificate Templates
C. The Security Configuration Wizard
D. The Certificates snap-in
Answer: A
QUESTION 313
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 has the DNS Server server role installed.
The network contains client computers that run either Linux, Windows 7, or Windows 8.
You have a zone named adatum.com as shown in the exhibit. (Click the Exhibit button.)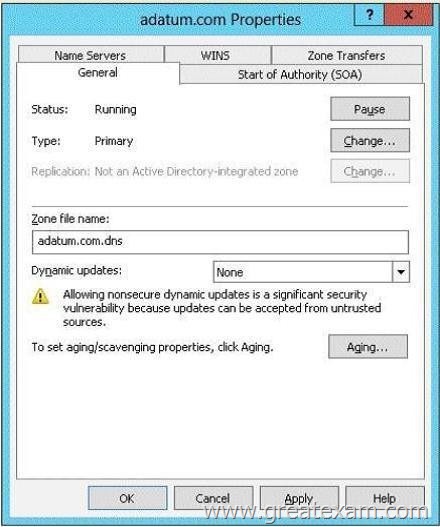
You plan to configure Name Protection on all of the DHCP servers.
You need to configure the adatum.com zone to support Name Protection.
Which two configurations should you perform from DNS Manager? (Each correct answer presents part of the solution. Choose two.)
A. Sign the zone.
B. Store the zone in Active Directory.
C. Modify the Security settings of the zone.
D. Configure Dynamic updates.
E. Add a DNS key record
Answer: BD
Explanation:
http://technet.microsoft.com/en-us/library/ee941152(v=ws.10).aspx
QUESTION 314
Your network contains two servers named Server1 and Server2 that run Windows Server 2008 R2. Server1 and Server2 are nodes in a failover cluster named Cluster1.
The network contains two servers named Server3 and Server4 that run Windows Server 2012 R2.
Server3 and Server4 are nodes in a failover cluster named Cluster2.
You need to move all of the applications and the services from Cluster1 to Cluster2.
What should you do first from Failover Cluster Manager?
A. On a server in Cluster2, configure Cluster-Aware Updating.
B. On a server in Cluster2, click Move Core Cluster Resources, and then click Best Possible Node.
C. On a server in Cluster1, click Move Core Cluster Resources, and then click Best Possible Node.
D. On a server in Cluster1, click Migrate Roles.
Answer: D
Explanation:
http://blogs.msdn.com/b/clustering/archive/2012/06/25/10323434.aspx
QUESTION 315
Your network contains an Active Directory domain named adatum.com.
The domain contains a file server named FS1 that runs Windows Server 2012 R2 and has the File Server Resource Manager role service installed.
All client computers run Windows 8.
File classification and Access-Denied Assistance are enabled on FS1.
You need to ensure that if users receive an Access Denied message, they can request assistance by email from the Access Denied dialog box.
What should you configure?
A. A file management task
B. A classification property
C. The File Server Resource Manager Options
D. A report task
Answer: C
QUESTION 316
Which security groups must a user account be a member of to modify the AD RMS SCP? (Choose two answers. Each answer forms part of a complete solution.)
A. Domain Admins
B. AD RMS Enterprise Administrators
C. Enterprise Admins
D. Cryptographic Operators.
Answer: BC
QUESTION 317
Which of the following would you configure if you wanted to block computers running Windows 7 and earlier operating systems from consuming AD RMS-protected content?
A. Trusted publishing domain
B. Trusted user domain
C. Exclusion policies
D. Super Users
Answer: C
QUESTION 318
Which of the following must you back up or have a copy of to be able to ensure that you can restore an AD RMS cluster in the event that a single server hosting all AD RMS components suffers complete data loss? (Choose three answers.)
A. Cluster key password
B. Trusted publishing domain
C. Trusted user domain
D. AD RMS databases
Answer: ABD
QUESTION 319
You want to enable key archiving on a CA.
You need to issue a certificate from a specific template to the user who will recover private keys. Which certificate template will you use as the basis for this certificate?
A. Kerberos authentication
B. Code signing
C. OCSP response signing
D. Key recovery agent
Answer: D
QUESTION 320
Which group policy item should you configure to enable automatic reenrollment of certificates?
A. Certificate Path Validation Settings
B. Certificate Services Client – Certificate Enrollment Policy
C. Certificate Services Client – Auto-Enrollment
D. Trusted Root Certification Authorities
Answer: C
The 70-412 PDF dumps and 70-412 practice test with free VCE player are available on GreatExam now. Get a complete hold of them through GreatExam to give your career a boost and start earning your Microsoft certification today!